Feature #13732
openAllow the use of macros within aliases
0%
Description
Because of limitation of IPv6 at the current way. (Traffic is allow between Vlan) I found a solution but this will be better if we can have more flexibility.
Can you make the option to create an Alias with Interface net and interface address.(drop down list) (same as when we create rules in destination drop down list) (ex: This Firewall, any, Alias or host, interface_name net....)
That way when we create a alias we choose Lan net, dmz net....
After that we can create a any rules with that alias.
There is my workaround about ipv6 traffic. 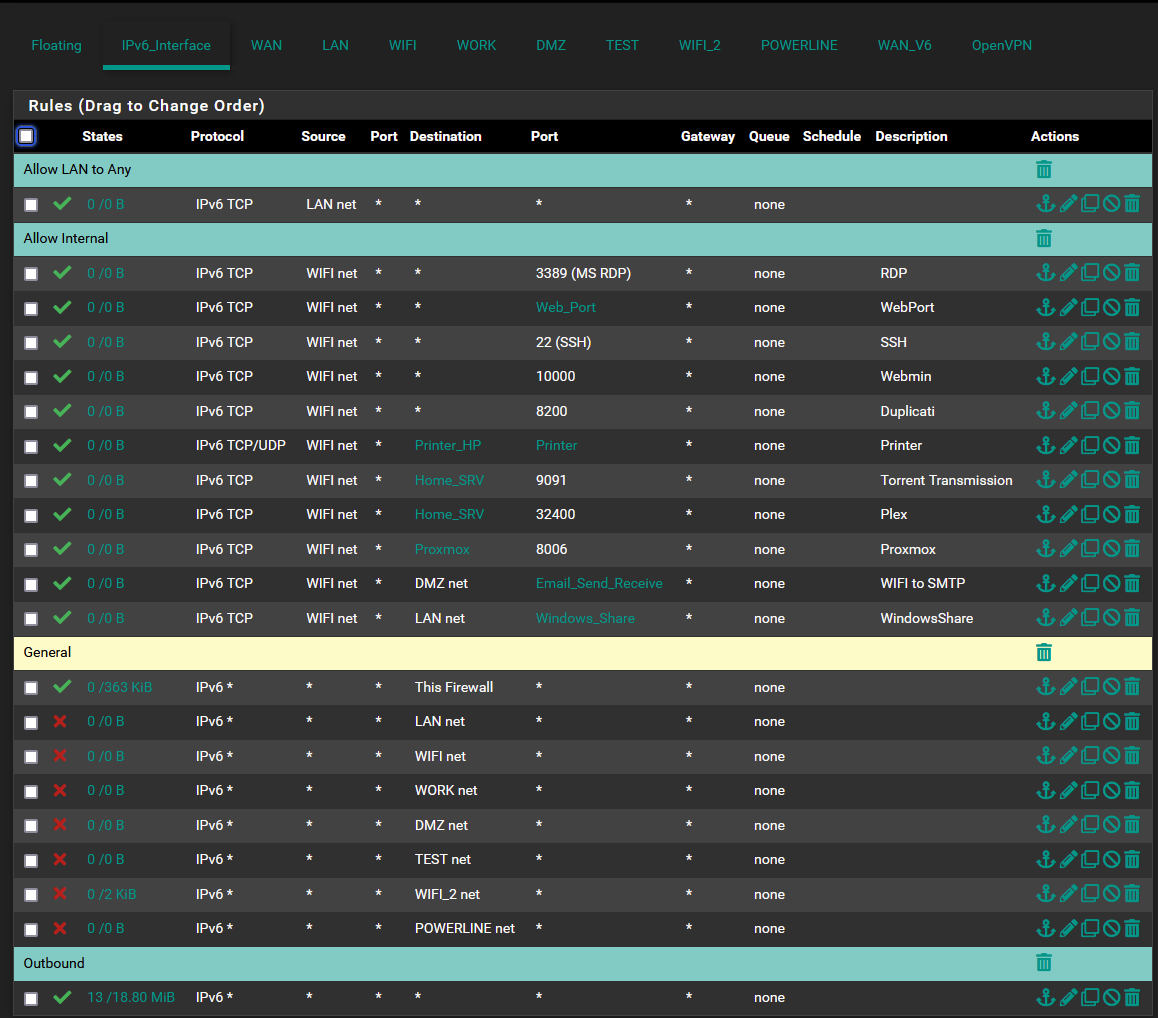
I create an interface group and add all local net. (Dynamic ipv6 from ISP)
Then create all rules for my need and it seem to work.
All other tab is reserved to IPv4 only.
If we can have alias as request the correct rules could be in tab interface instead of having lots of deny rules.
Best way to have the same behavior as we have in ipv4 (block all communication between vlan).
Files
Related issues
 Updated by Marcos M about 3 years ago
Updated by Marcos M about 3 years ago
- Subject changed from Allow to create an Alias with interface to Allow the use of macros within aliases
- Priority changed from Normal to Very Low
The * net and * address options are actually macros, not aliases, which are handled differently by the system. It may be possible to implement that feature, but that would likely add more failure points and complexity. That doesn't seem to be worth the benefit when one can simply have multiple rules which clearly show what's being filtered.
 Updated by Luc Courville about 3 years ago
Updated by Luc Courville about 3 years ago
I understand but this is a easy way to help everyone.
Let me give you an exemple
If you have 10 interface that mean if you don't create an interface group you need to create 100 rules just for blocking inter vlan. That doesn't make any sense for me. If you miss something your security is compromise.
Another solution is to permit to add multiple source/destination inside single rules. Alias will be better because you just modify the alias one time. At least you did not create lots of rules.
Another one is to add in source/destination an objet with all local net except wan (same as this firewall (self) (that is ip instead of net).
I work with other firewall and some have an objet Wan (internet) (probably everything except all lan network configured). I think this is also a good way to build rules.
With pfsense you need to create a rules for internet that is any to any and include everything even local. In ipv4 you could specify the gateway that will block internal but not in ipv6 world.
 Updated by Luc Courville about 3 years ago
Updated by Luc Courville about 3 years ago
In ipv6 we now receive public ip locally and this is dynamic.
The old way to block private IP is not an option with ipv6 with dynamic ISP with multiple internal interface.
 Updated by Marcos M about 3 years ago
Updated by Marcos M about 3 years ago
I agree it can be tedious. There's the Copy button on the rules page which does make it easier.
 Updated by Marcos M over 2 years ago
Updated by Marcos M over 2 years ago
- Related to Feature #3288: Support interface macros in Outbound NAT rules added