Feature #15244
openModern authentication via FIDO2 for local account authentication
0%
Description
Implementation of FIDO2 WebAuthN capabilities into RELENG_2_7_2.
WHAT
FIDO2 adds convenient phishing-resistant multifactor authentication to pfsense webui for local accounts.
With this implementation, you can use passkeys, pin, and biometrics from device platform (e.g. Windows Hello) or roaming devices (e.g. yubikey).
For more info visit - https://fidoalliance.org/fido2/
WHY
pfSense should have phishing-resistant multifactor authentication capabilities. Since W3C implementation of WebAuthN & CTAPv2 this is now possible in most modern browsers and platform devices, and therefore capable within pfsense.
FIDO2 is becoming industry standard replacement for password-based authentication (Google, Microsoft, Meta). This will add additional security protections and value with little to no impact to the product.
Implementation Fork from RELENG_2_7_2
https://github.com/TheUniquePaulSmith/pfsense/tree/devel/modern_auth
- pfSense must be in HTTPS mode with FQDN to be capable of FIDO2 registrations & authentications
- Browsers must support WebAuthN (most do https://developer.mozilla.org/en-US/docs/Web/API/Web_Authentication_API#browser_compatibility )
- Registering device must support platform authenticator (most do.. Windows 10\11, macOS, iOS, Android)
- I opted not to make this a package as it should be core offering of the product and webui\system_usermanager itself (also needed to modify login page to support FIDO2)
- FIDO2 attestations use php openssl_verify as core authentication mechanism
- FIDO2 is a more secure login mechanism, but needs to co-exist with Forms-based password login for now
- Modifications to account creation page to support registration of platform-based FIDO2 credentials
- Registrations are stored in an array $confg->system->user->fido2entries
- Users can (and should) register multiple FIDO2 devices (typically in case of lost device)
- I wanted to make minimally invasive injection of FIDO2, therefore only the login page, and system_usermanager UIs were changed
- I tried my best to follow the php coding standards and practice that has been laid out, essentially, I cloned password-based login with fido2 capabilities in auth code
- Need to fix reg & auth challenge validation
- You can only register and delete FIDO2 registrations and not edit them
- If admin changes the FQDN of pfSense, all existing registrations will become invalid since they are tied to relying party
- Registration process is kind of clunky since I tried to fit it into the system_usermanager POST requests. Essentially you create a registration on your device, then "Save" it on a user which is processed by the server. Can lead to a state where user doesn't click Save but a passkey on the device was already created (and not saved on the server)
- FIDO2 registrations are tied to existing users, therefore you must create a user first before being able to register a device
- I only implemented platform based registration, but should be easy to allow cross-platform (roaming) registrations
- I use javascript prompt (yuck) to capture friendly description during registration. Might be better to build separate page\tab (like how certificates work)
- Not great with javascript & php encoding formats, so there is probably unnecessary encoding handling from client to server
Sign-In Page after clicking Link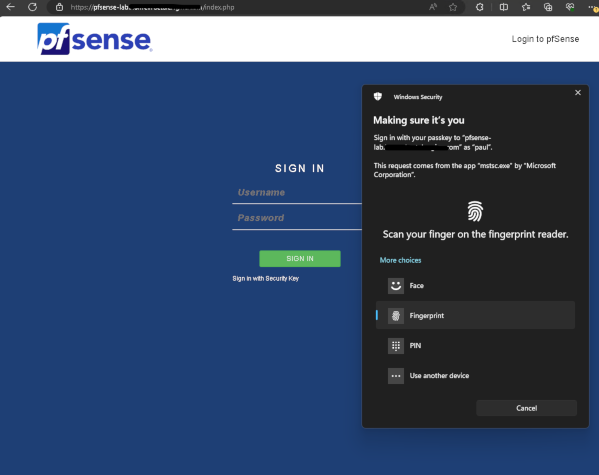
Registering new FIDO2 credential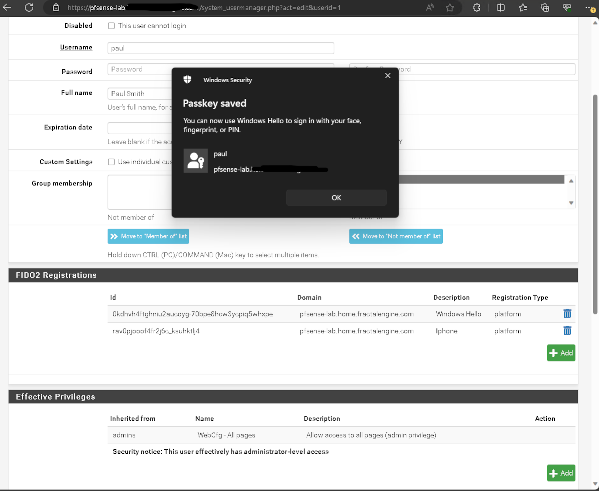
refer to the following article to manage passkeys in Windows 11: https://support.microsoft.com/en-us/windows/passkeys-in-windows-301c8944-5ea2-452b-9886-97e4d2ef4422
Files
 Updated by Kris Phillips about 2 years ago
Updated by Kris Phillips about 2 years ago
Duplicate of https://redmine.pfsense.org/issues/14743
 Updated by Sergei Shablovsky over 1 year ago
Updated by Sergei Shablovsky over 1 year ago
UPVOTE THIS
Nowadays with numbers of hacking attacks rapidly increasing each day, securing the access to firewall (especially border, - the core of company security infrastructure) itself by VPN/SSH become #1.
(Of course with additional monitoring and alerting tool).
Todays leader for both Personal and Enterprise’s MFA marker are YubiKeys https://www.yubico.com/products/,- PERFECT DEVELOPED, WELL INGENEERED and W/O ANY COMPROMISING ISSUES on a millions of customers.
So, reasonable to securing ALL THREE local physical VGA terminal, SSH terminal and WebGUI access by YubiKey 5 Series (https://www.yubico.com/products/yubikey-5-overview/, PDF https://resources.yubico.com/53ZDUYE6/as/q3uxbe-6n9olc-9ywi4w/YubiKey_5_Series_Product_Brief.pdf, latest model line).
Well-documented (https://docs.yubico.com/ all official docs) API, SDK, and a lot of ready (and well tested by thousands of professionals in security) code https://www.google.com/search?q=YubiKey+FreeBSD&ie=UTF-8&oe=UTF-8&hl=en&client=safari#ip=1 (most valuable are links on FreeBSD user forum and GitHub).
I hope all this facts help Netgate (as one of the leaders of industry) to obtain extra value for their pfSense+ and CE products.