Feature #14196
openpermitted firewall rules - additional text
0%
Description
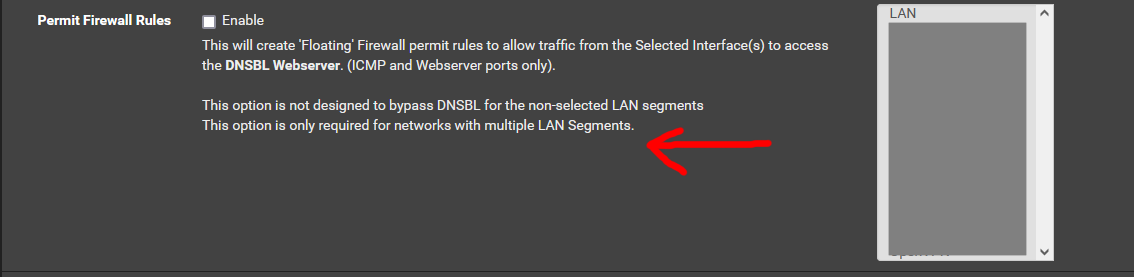
Firewall --> pfBlockerNG --> DNSBL --> DNSBL Configuration --> Permit Firewall Rules
Can you add some additional information here for the end user to explain lan segment and some possible scenarios when you would use this option.
https://networkencyclopedia.com/lan-segment/ - Lan Segment is a physical portion of a local area network (LAN) that is separated from other portions by bridges or routers.
https://www.reddit.com/r/pfBlockerNG/comments/p9te6f/should_permit_firewall_rules_be_enabled_i_was/ - This thread mentions that you do not need this option unless you have VLANs
Files
 Updated by Kris Phillips almost 3 years ago
Updated by Kris Phillips almost 3 years ago
- Status changed from New to Incomplete
Based on the text above this line, this is simply moving the rules from the one interface to a floating rule for multiple interfaces. What would you like added to this section for clarification?
 Updated by Jon Brown almost 3 years ago
Updated by Jon Brown almost 3 years ago
- Based on the text above this line, this is simply moving the rules from the one interface to a floating rule for multiple interfaces.
- I am not sure your statement is correct. This creates a rule, does not move any
- This still does not shine any light on this feature
- I do not have this feature enabled and there are no rules created by pfBlockerNG on my individual interfaces
- why is this only needed on networks with multiple LAN segments? This is why a scenario here would explain the use of this. The following are some guesses/examples:
- You would only use this option when you have your LAN (Network) split into several segments (i.e. ................So those segments can ping and connect to the 'DNSBL Webserver' which otherwise would be blocked by the firewall to them. If you cannot ping.........this happens......... and if you cannot connect to the 'DNSBL Webserver' you will get connection errors display in your browser.
- You would only use this option when you have your LAN (Network) split into several segments because certain IP routing information is stripped and the DNSBL Webserver cannot determine the traffic correctly as it is blocked before being processed....
- The traffic on other LAN segments is crossing a firewall boundry/interface before reaching the 'DNSBL Webserver' on the LAN segment and this allows the traffic to pass so it can get processed.
The links above were for context and to show I had looked into this :)
I am only guessing here what this does and that is the problem, I cannot figure out the edge case for this option. i.e. why is ping allowed, I cant see the point. If I could I could give you some better text, Catch22 situation.
thanks