Bug #13940
closedFirewall log parser does not handle SCTP log entries
100%
Description
Tested in 22.05 / 23.01.
The firewall logs page in the webGUI does not show the following entries in /var/log/filter.log:
Feb 6 12:27:26 pfs-firewall-1 filterlog[24979]: 213,,,1663257066,vtnet8,match,block,in,4,0xa0,,254,17063,0,none,132,sctp,60,198.51.100.131,192.0.2.110,datalength=40
Files
Related issues
 Updated by Jim Pingle about 3 years ago
Updated by Jim Pingle about 3 years ago
- Subject changed from webGUI Firewall Logs do not show SCTP entries to Firewall log parser does not handle SCTP log entries
- Category changed from Web Interface to System Logs
- Target version set to 2.7.0
- Plus Target Version set to 23.05
The protocol layout isn't defined in the log parser so it doesn't know what to do with it. There is no test for protocol 132 in the block at source:src/etc/inc/syslog.inc#L1101 in parse_firewall_log_line()
There could maybe be a default test at the end to catch unknown protocols, like the IGMP section could be moved down and the protocol check removed from that, so unknown protocols just show source/destination address and no other data.
While there, that whole block should really be a switch statement and not a bunch of if/elseif checks.
 Updated by Théo Sarrazin about 3 years ago
Updated by Théo Sarrazin about 3 years ago
 Updated by Jim Pingle about 3 years ago
Updated by Jim Pingle about 3 years ago
- Status changed from New to Pull Request Review
 Updated by Jim Pingle almost 3 years ago
Updated by Jim Pingle almost 3 years ago
- Plus Target Version changed from 23.05 to 23.09
 Updated by Jim Pingle over 2 years ago
Updated by Jim Pingle over 2 years ago
- Status changed from Pull Request Review to Feedback
- % Done changed from 0 to 100
PR merged
 Updated by Jim Pingle over 2 years ago
Updated by Jim Pingle over 2 years ago
- File clipboard-202306121058-vs7st.png clipboard-202306121058-vs7st.png added
- File clipboard-202306121101-x7fpj.png clipboard-202306121101-x7fpj.png added
- Status changed from Feedback to Resolved
Seems to be working OK. Logs are showing not only SCTP but also some other entries that were not previously parsed.
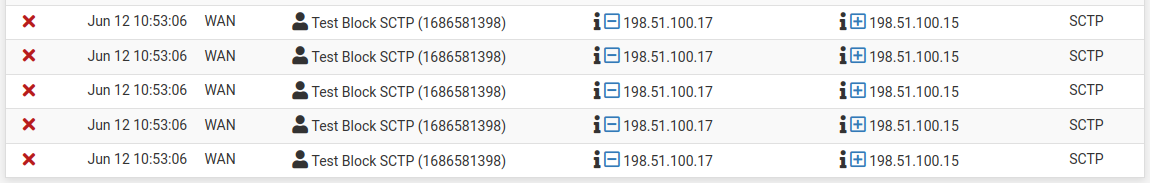
Not sure if we want to keep these in the (visible GUI) log or suppress them, but that can be left up to another Redmine request:
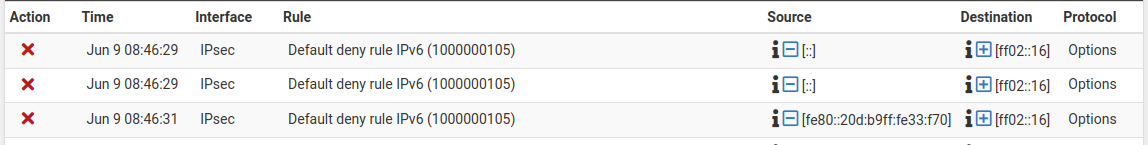
The GUI is accurately displaying what is in the filter.log file for those lines, so it's also possible something in filterlog needs adjusted for those entries. Either way it's outside the scope of this issue.
 Updated by Jim Pingle over 2 years ago
Updated by Jim Pingle over 2 years ago
- Related to Feature #14667: Improve SCTP support in ``filterlog`` added