Actions
Bug #16138
closedEthernet rules passing IPv4 (0x0800) packets despite the block rule
Status:
Not a Bug
Priority:
Normal
Assignee:
-
Category:
Rules / NAT
Target version:
-
Start date:
Due date:
% Done:
0%
Estimated time:
Release Notes:
Default
Affected Plus Version:
Affected Architecture:
Description
Tested on 24.11 and 25.03 Beta built on Fri Apr 4
Setup:
ix2 and igb1 in bridge, filtering on member interface:
net.link.bridge.pfil_onlyip=0
net.link.bridge.pfil_member=1
net.link.bridge.pfil_bridge=0
Any to any rules on ix2 and igb1
pass in quick on ix2 inet all flags S/SA keep state (if-bound) label "USER_RULE" label "id:1744382074" ridentifier 1744382074
pass in quick on igb1 inet all flags S/SA keep state (if-bound) label "USER_RULE" label "id:1744386976" ridentifier 1744386976
Ethernet rule:
ether block on ix2 proto 0x0800 l3 all label "id:1744386799" ridentifier 1744386799
I can see the traffic counters however the IPv4 ICMP packets are still passing
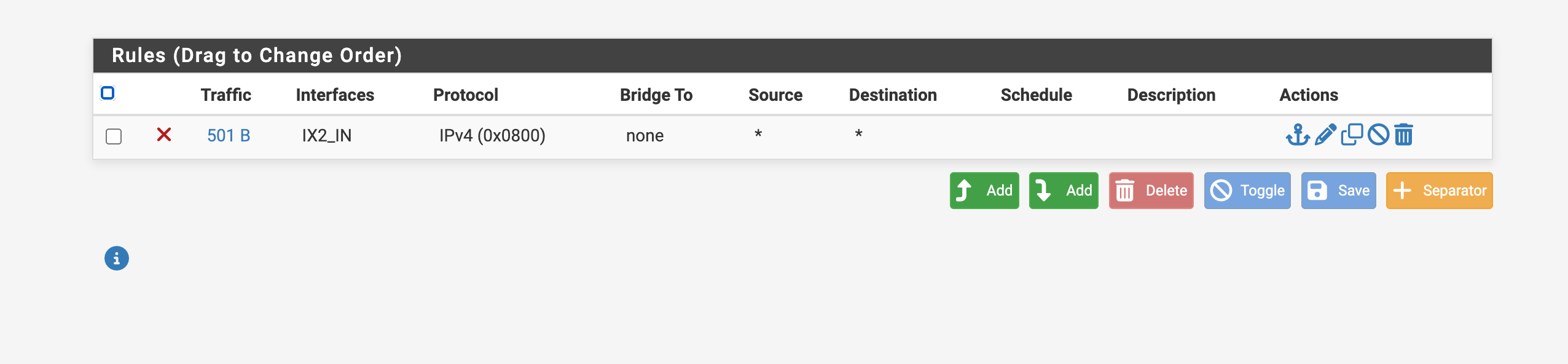
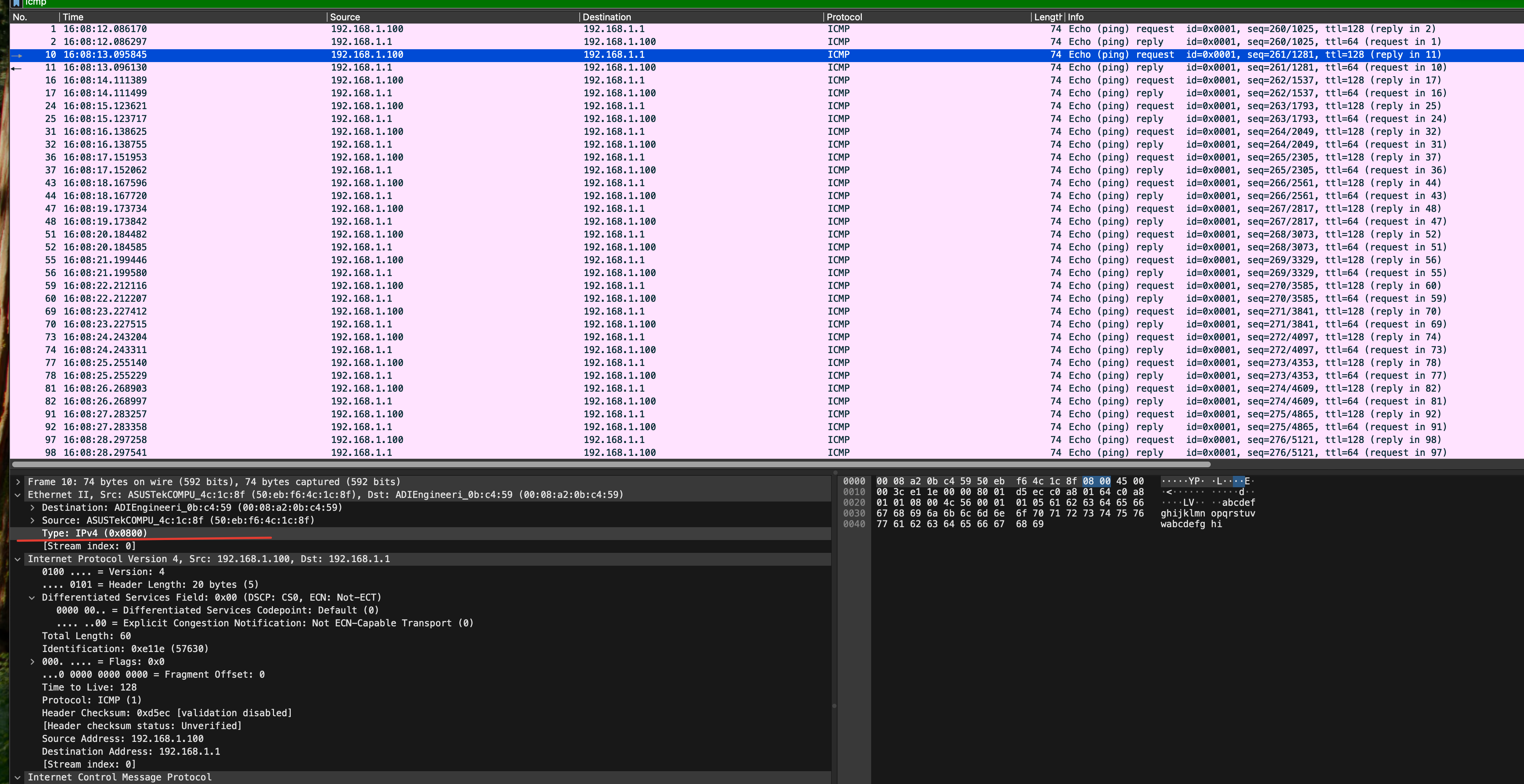
Files
 Updated by Lev Prokofev 9 months ago
Updated by Lev Prokofev 9 months ago
- Project changed from pfSense to pfSense Plus
- Category changed from Rules / NAT to Rules / NAT
 Updated by Boris Pavlovic 8 months ago
Updated by Boris Pavlovic 8 months ago
If you set
net.link.bridge.ipfw=1 (it was set to 0 by default)
Ethernet rules start to function
Tested on
Netgate 6100 and 23.05.1
 Updated by Steve Wheeler 8 months ago
Updated by Steve Wheeler 8 months ago
- Status changed from New to Not a Bug
Yes exactly that. You must set net.link.bridge.ipfw to 1 to enable link-level pfil hooks on the bridge.
With that set it filters as expected.
Tested: 25.03-beta.
 Updated by Jim Pingle 8 months ago
Updated by Jim Pingle 8 months ago
I added a note about that tunable to the docs (in Bridging, but with an xref in Ethernet rules).
Actions