Bug #16194
openIPv6 ICMP firewall log entries marked with protocol "Options" instead of ICMPv6
0%
Description
Firewall log entries for ICMPv6 packets are showing a value of "Options" in the Protocol column, but only on development snapshots (Plus 25.07, CE 2.9.0).
Plus 25.03 and CE 2.8.0 builds are not affected.
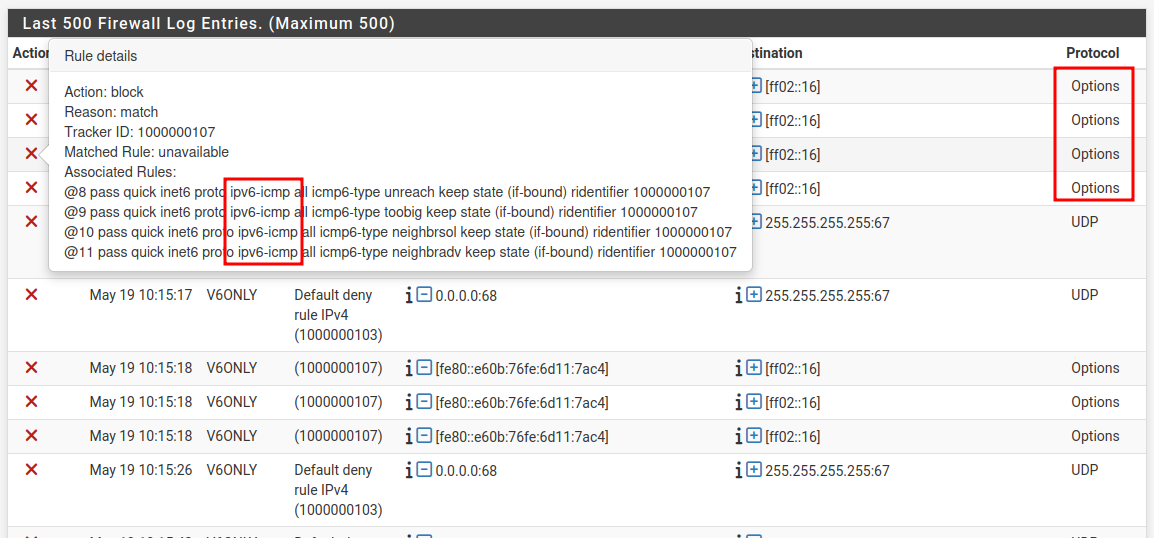
This may be something that changed in PF and possibly being misinterpreted by pflog/filterlog since that is what shows in the actual log.
Plus 25.07/CE 2.9.0 have this entry in filter.log:
filterlog[68725]: 8,,,1000000107,vtnet1,match,block,in,6,0x00,0x00000,1,Options,0,36,fe80::ae1a:a270:e35e:439b,ff02::16,HBH,RTALERT,0x0000,PADN,
A working log entry from Plus 25.03/2.8.0 looks like this:
filterlog[61925]: 6,,,1000000105,vtnet2,match,block,in,6,0x00,0x00000,1,ICMPv6,58,48,fe80::f847:aeff:fe06:1cbd,ff02::16,
Files
 Updated by Jim Pingle 6 months ago
Updated by Jim Pingle 6 months ago
- Plus Target Version changed from 25.07 to 25.11
 Updated by Jim Pingle 6 months ago
Updated by Jim Pingle 6 months ago
- File clipboard-202507071118-cesbl.png clipboard-202507071118-cesbl.png added
- Status changed from Feedback to Confirmed
This is still happening, but now I was able to reproduce it on 25.07 (was 25.03). It's not every ICMPv6 just certain types.
Raw log entry:
Jul 7 11:16:03 pmx-25-07 filterlog[88995]: 6,,,1000000105,vtnet2,match,block,in,6,0x00,0x00000,1,Options,0,36,fe80::xxxx:xxxx:xxxx:68b4,ff02::16,HBH,PADN,RTALERT,0x0000,
Firewall rule that produced the log:
@6 block drop in log inet6 all label "Default deny rule IPv6" ridentifier 1000000105
I have a packet capture of a packet which generates this log entry and can reproduce it on demand (happens when a macOS device boots on the segment, at a minimum):
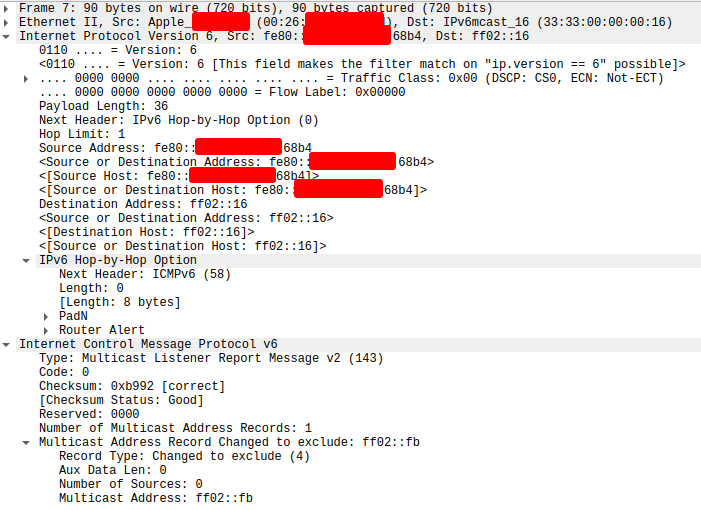
 Updated by Jeff Earickson 5 months ago
Updated by Jeff Earickson 5 months ago
I am also seeing this on an 1100 after updating from 24.11 to 25.07 (released Aug 4). My /var/log/filterlog lines look like:
Aug 5 16:38:02 cleo filterlog: 247,,,1649447902,mvneta0.4092,match,block,in,6,0x00,0x00000,1,Options,0,36,fe80::417:952d:77be:4497,ff02::16,HBH,PADN,RTALERT,0x0000,
Rule(s) 1649447902 look like:
pfctl -sr | grep 1649447902
block drop in log quick on mvneta0.4092 inet all label "USER_RULE: OPT Reject (last rule)" label "id:1649447902" ridentifier 1649447902
block drop in log quick on mvneta0.4092 inet6 all label "USER_RULE: OPT Reject (last rule)" label "id:1649447902" ridentifier 1649447902
It is the last rule in the ruleset for the interface. I have seen the same behavior from an identical rule for LAN. I have tried toggling the "Allow IP Options" advanced setting for the rule on and off -- no change.
Like Jim Pingle, I have a house full of Apple devices: two Macs and two Iphones. Booting up a Mac will produce a burst of these logs.
 Updated by Jim Pingle 2 months ago
Updated by Jim Pingle 2 months ago
- Plus Target Version changed from 25.11 to 26.03
 Updated by Marcos M about 1 month ago
Updated by Marcos M about 1 month ago
- Category changed from System Logs to Logging
- Target version changed from 2.9.0 to CE-Next
- Plus Target Version changed from 26.03 to Plus-Next
This looks to be an issue with filterlog not decoding protocol 58 (IPv6-ICMP) when it sees protocol 0 (HOPOPT). I expect this has always been the case but is now visible due to an upstream fix/change to show these block reasons.
 Updated by Jeff Earickson 29 days ago
Updated by Jeff Earickson 29 days ago
This bug is alive and well in 25.11. I saw it pop up the other day on a Netgate 2100 after upgrade from 25.07.01 to 25.11.