Bug #16329
closedECDSA key file missing when exporting a Viscosity bundle with a password protected certificate
100%
Description
In the same vain as #15086, today I had cause to export a OpenVPN client profile. As an extra layer of protection I ticked "Password Protect Certificate", provided a password and clicked "Viscosity Bundle".
The resulting "XXXX-Viscosity.visc.zip" file was missing the key.key file.
I have access to a number of different pfsense firewalls here, of differing ages. The older ones, which all have RSA based PKI all include a key.key when I export a "Viscosity Bundle" with "Password Protect Certificate" ticked. The firewalls which have been more recently deployed are using EC based PKI and when I export a "Viscosity Bundle" with "Password Protect Certificate" ticked the exports are missing the key.key file.
I suspect the root cause is line 823 in https://github.com/pfsense/FreeBSD-ports/blob/devel/security/pfSense-pkg-openvpn-client-export/files/usr/local/pkg/openvpn-client-export.inc
exec("/usr/bin/openssl rsa -in ${eclearkeyfile} -out ${ekeyfile} -des3 -passout pass:${eoutpass}");
There's a clear assumption the key is RSA.
As a test, I downloaded the bundle without "Password Protect Certificate" ticked and attempted to encrypt the key manually and got an error...
/usr/bin/openssl rsa -in key.key -out key2.key -des3 -passout pass:example_password Not an RSA key
If I change the command to use ec, it works...
/usr/bin/openssl ec -in key.key -out key2.key -des3 -passout pass:example_password read EC key writing EC key
Sadly, I've been unable to find a decent way to determined if a key is RSA or ECA. The closes I've come is...
$ openssl pkey -in key.key -text -noout | head -n 1 Private-Key: (256 bit) $ openssl pkey -in rsa.key -text -noout | head -n 1 Private-Key: (4096 bit, 2 primes)
and then maybe assume if the output mentioned primes it'll be RSA key?
Files
 Updated by aleksei prokofiev 6 months ago
Updated by aleksei prokofiev 6 months ago
Tested on 25.07 with openvpn-client-export 1.9.5
25.07-RELEASE (amd64)
built on Wed Jul 23 0:24:00 +04 2025
FreeBSD 15.0-CURRENT
Can not reproduce, the key.key file always presented doesn't matter enabled or not Password Protect Certificate
 Updated by Steve Scotter 6 months ago
Updated by Steve Scotter 6 months ago
- File clipboard-202508131811-khi2a.png clipboard-202508131811-khi2a.png added
- File clipboard-202508131814-gdtqa.png clipboard-202508131814-gdtqa.png added
- File clipboard-202508131823-jphup.png clipboard-202508131823-jphup.png added
I'm not sure what to say, I'm able to reproduce the issue on demand.
My environment is currently running 24.11, but openvpn-client-export is version 1.9.5 which I think is all that matters.
The CA I'm using for my OpenVPN server was internally created by pfsense and has a key type of ECDSA.
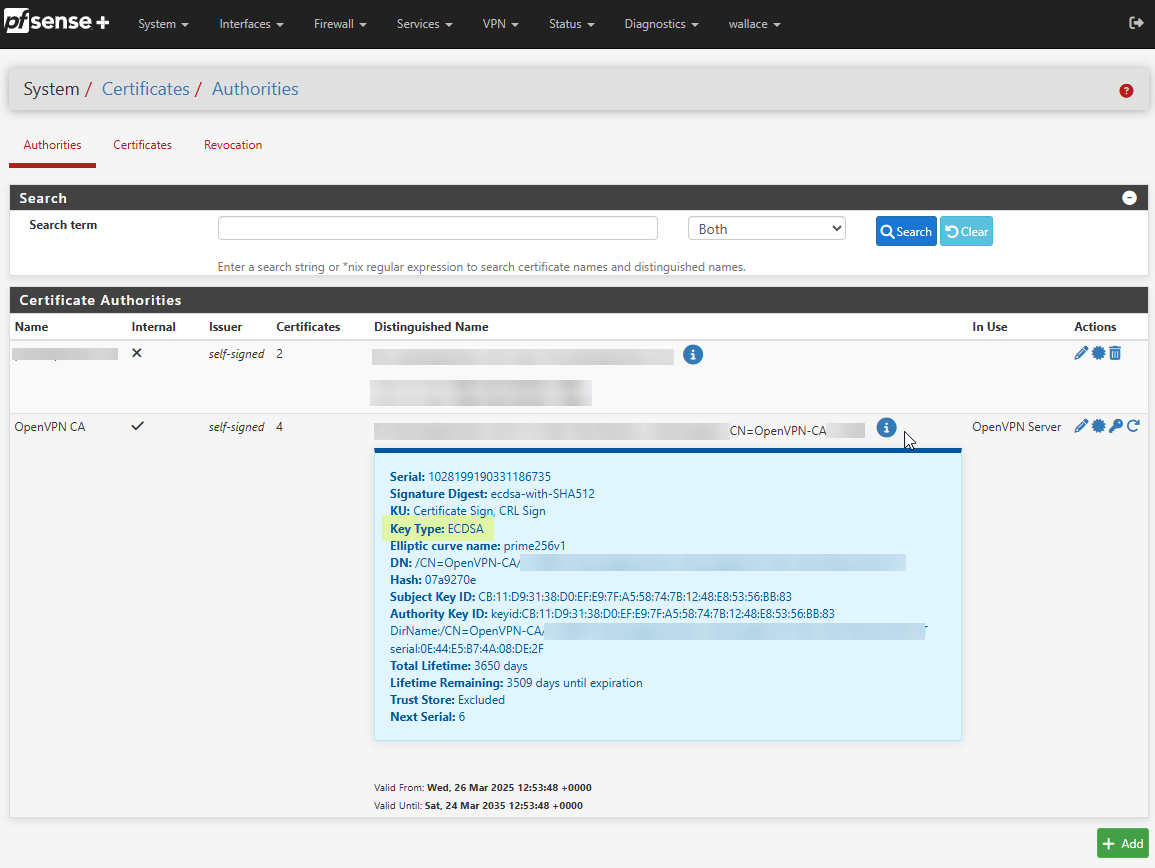
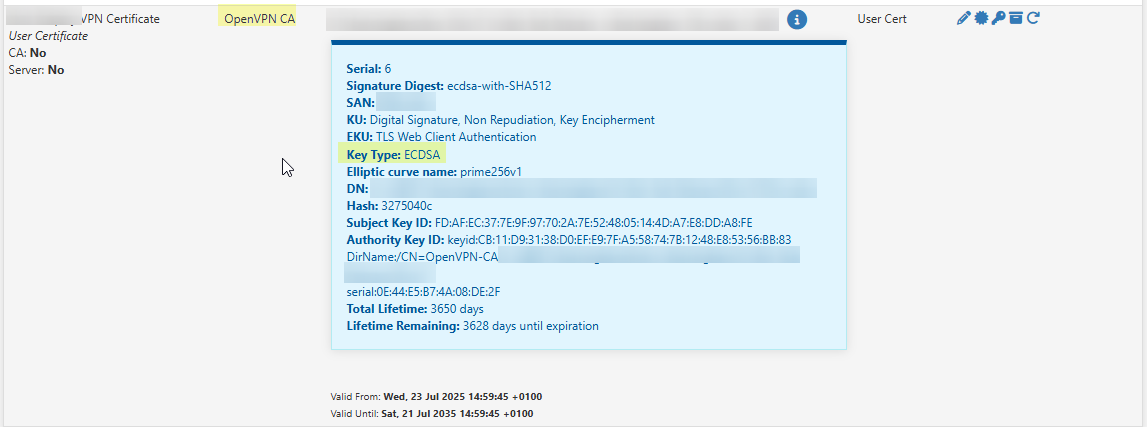
The certificate for the user I'm trying to create a password protected Viscosity bundle is singed by the above CA and also has a key type of ECDSA.
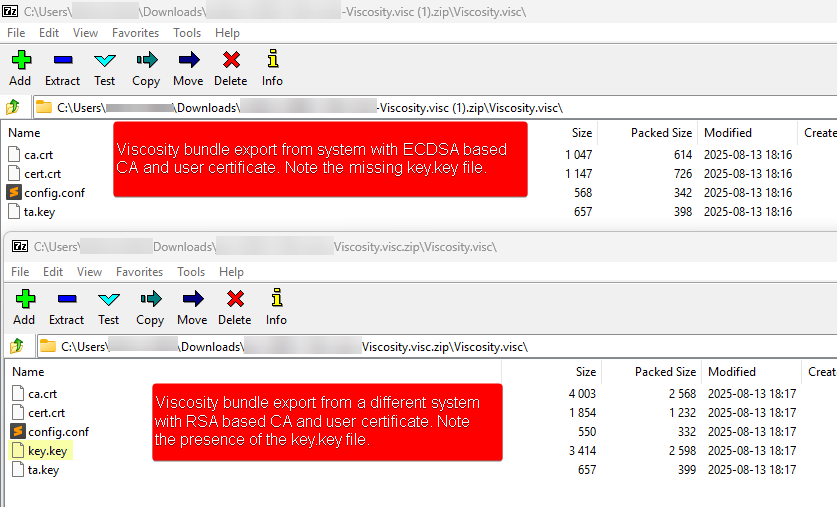
Below are screenshots of Viscosity bundles exported from two different systems. The top one is the system I'm having problems with and it's PKI is ECDSA based. The bottom one is a older system which whos PKI is RSA based.
Happy to help however I can. What else can I provide you to assist you reproducing the bug in your environment? Happy to jump on a screensharing session if it'll help.
Thanks
Steve
 Updated by Steve Scotter 6 months ago
Updated by Steve Scotter 6 months ago
Today I've upgraded the firewalls in question from 24.11 to 25.07.1 and retested exporting EC. The same thing happens when downloading a Viscosity bundle... i.e., there is no key.key file in the Zip.
 Updated by Danilo Zrenjanin 5 months ago
Updated by Danilo Zrenjanin 5 months ago
- Status changed from New to Confirmed
Tested against:
25.07.1-RELEASE (amd64) built on Fri Aug 15 18:42:00 UTC 2025 FreeBSD 15.0-CURRENT
I can confirm the reported issue. By default, the wizard generates certificates with the RSA key type. To reproduce the problem, the ECDSA key type must be manually selected for both the CA and user certificates.
 Updated by Steve Scotter 4 months ago
Updated by Steve Scotter 4 months ago
While working on an entirely different project I found some code which detects private key type and instantly thought of this bug report...
$typeNames = [
OPENSSL_KEYTYPE_RSA => 'RSA',
OPENSSL_KEYTYPE_DSA => 'DSA',
OPENSSL_KEYTYPE_DH => 'DH',
OPENSSL_KEYTYPE_EC => 'Elliptic Curve (EC)',
];
$privateKeyPath = Yii::getAlias('@app/runtime/saml.key');
if (!file_exists($privateKeyPath)) {
echo "Private key not found at: {$privateKeyPath}";
return;
}
$keyContent = file_get_contents($privateKeyPath);
$keyResource = openssl_pkey_get_private($keyContent);
if (!$keyResource) {
echo "Unable to load private key (possibly password-protected or invalid)";
return;
}
// Extract key details
$keyDetails = openssl_pkey_get_details($keyResource);
$type = $typeNames[$keyDetails['type']] ?? 'Unknown';
echo "Key Type: {$type}\n";
echo "Key Size: {$keyDetails['bits']} bits\n";
In principle the above logic could be used to detect the key type and then decide whether to execute /usr/bin/openssl rsa -in key.key -out key2.key -des3 -passout pass:example_password or /usr/bin/openssl ec -in key.key -out key2.key -des3 -passout pass:example_password
If I get a chance I'll have a look at creating a patch myself, but in the likely event I don't, this may help someone move this issue forward. TIA.
 Updated by Jim Pingle 2 months ago
Updated by Jim Pingle 2 months ago
- Status changed from Confirmed to In Progress
- Assignee changed from Christian McDonald to Jim Pingle
 Updated by Jim Pingle 2 months ago
Updated by Jim Pingle 2 months ago
- Subject changed from openvpn-client-export 1.9.5 | Viscosity Bundle | ECDSA cert missing key when Password Protect Certificate is ticked to ECDSA key file missing when exporting a Viscosity bundle with a password protected certificate
 Updated by Jim Pingle 2 months ago
Updated by Jim Pingle 2 months ago
We already have code in other places that detects the key type, it's simple enough to do something like this here:
$prvkey = base64_decode($cert['prv']);
$key_details = openssl_pkey_get_details(openssl_pkey_get_private($prvkey));
$keytype = ($key_details['type'] == OPENSSL_KEYTYPE_RSA) ? 'rsa' : 'ec';
// [...]
exec("/usr/bin/openssl {$keytype} -in {$eclearkeyfile} -out {$ekeyfile} -des3 -passout pass:{$eoutpass}");
 Updated by Jim Pingle 2 months ago
Updated by Jim Pingle 2 months ago
- Status changed from In Progress to Resolved
- % Done changed from 0 to 100
Fixed in the latest OpenVPN client export package build.