Bug #13045
openFirewall floating rules ignore WireGuard traffic
0%
Description
When adding a floating rule to apply a limiter targeting traffic on a WireGuard interface, the rule is ignored.
Add a new rule:
Action: pass
Interface: WG0
Direction: out
Gateway: WG0_GW
In/Out Pipe: WGDownQ / WGUpQ
Counters show 0 / 0 for states and traffic regardless of rule order, direction, or gateway specified.
Additionally, if a rule is added on a WAN interface targeting the IP of a remote wireguard peer, the rule is ignored only when a WireGuard peer is active for that same IP.
Action: pass
Interface: WAN
Direction: out
Source (or Destination): address x.x.x.x
Gateway: WAN_GW
In/Out Pipe: WANDownQ / WANUpQ
Counters show 0 / 0 for states and traffic regardless of rule order, direction, or gateway specified.
Files
 Updated by → luckman212 over 3 years ago
Updated by → luckman212 over 3 years ago
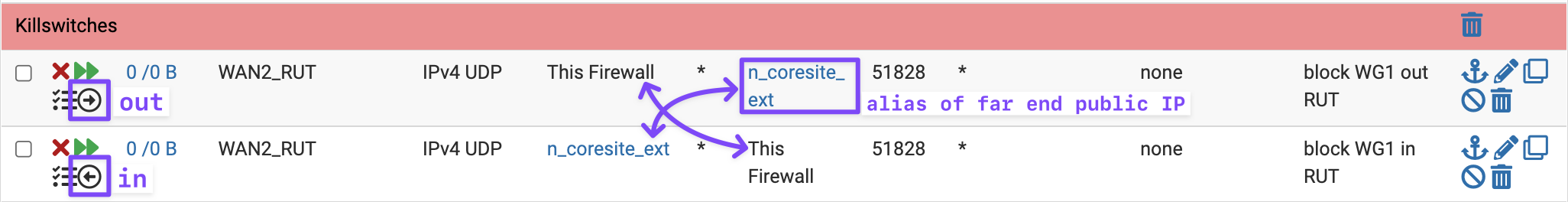
Christian McDonald can you comment on whether rules (specifically block rules) are working for assigned Wireguard interfaces, or Floating Rules? I'm having a heck of a time with trying to lock one of my site-to-site tunnels to a specific WAN: Block Wireguard site-to-site traffic via a certain WAN
I'm not running 22.11 yet, but will happily test if there are any important changes there that might affect this.
 Updated by → luckman212 over 3 years ago
Updated by → luckman212 over 3 years ago
edit: I was able to make it work for now by making sure to kill states and then having this pair of quick/block floating rules (one for each direction)