Feature #14265
closed
Option to invalidate GUI login session if the client address changes
Added by Jim Pingle almost 3 years ago.
Updated over 2 years ago.
Plus Target Version:
23.09
Description
Currently once the user logs in, their session is valid even if the client source address changes. This allows the user to roam if they happen to change WANs (e.g. client behind multi-WAN load balancing, CGN, cell network, etc) or if they access by hostname and have to downgrade from IPv6 to IPv4. However, this behavior is less secure than invalidating the session if the client address changes, forcing the user to log back in if the address changes. This is largely moot for most users however as they should be accessing the firewall over a VPN or local management network and the address is less likely to change in those cases, making it safer to activate.
Having the option to enable this strict behavior would be good from a security standpoint, though I am hesitant to activate it by default given the potential for disruption.
Files
- Description updated (diff)
- Status changed from New to Pull Request Review
- Assignee set to Christopher Cope
- Status changed from Pull Request Review to Feedback
- % Done changed from 0 to 100
I conducted a test on the commit, however, altering the client source IP address did not result in a connection break. I double-checked and ensured that the Roaming option was unchecked.
Please check.
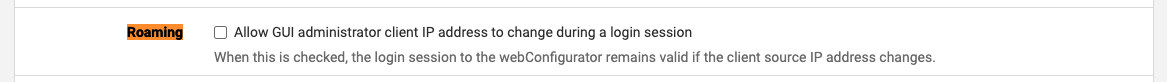
I tested it multiple times on multiple clients and it always kicked me off. Are you sure the client address is changing from the perspective of the firewall? Check the client info displayed on the dashboard, it will show the username and client IP address there in the system info widget.
I used a client on LAN and changed its DHCP reservation and restarted networking on the client which ensured it moved to the new address, then tried to refresh the browser page. With roaming enabled I could keep accessing the GUI. With roaming disabled I was always kicked out to the login screen. The client may play a factor here as well since it has to move to a new address, using a static address might be a simpler test depending on the client OS. I used a Linux client where it was a pretty simple off/on toggle of the interface networking to make it pick up the address change.
- Status changed from Feedback to Resolved
I've just tested again applying the patch on a clean install. It works as expected.
Tested against:
2.7.0-RELEASE (amd64)
built on Wed Jun 28 03:53:34 UTC 2023
FreeBSD 14.0-CURRENT
I am marking this ticket resovled.
- Target version changed from CE-Next to 2.8.0
- Plus Target Version changed from Plus-Next to 23.09
- Target version changed from 2.8.0 to 2.7.1
Also available in: Atom
PDF
