Bug #14531
openTraffic Graph widget doesn't show traffic counts for OpenVPN interfaces since 23.05.1 upgrade.
0%
Description
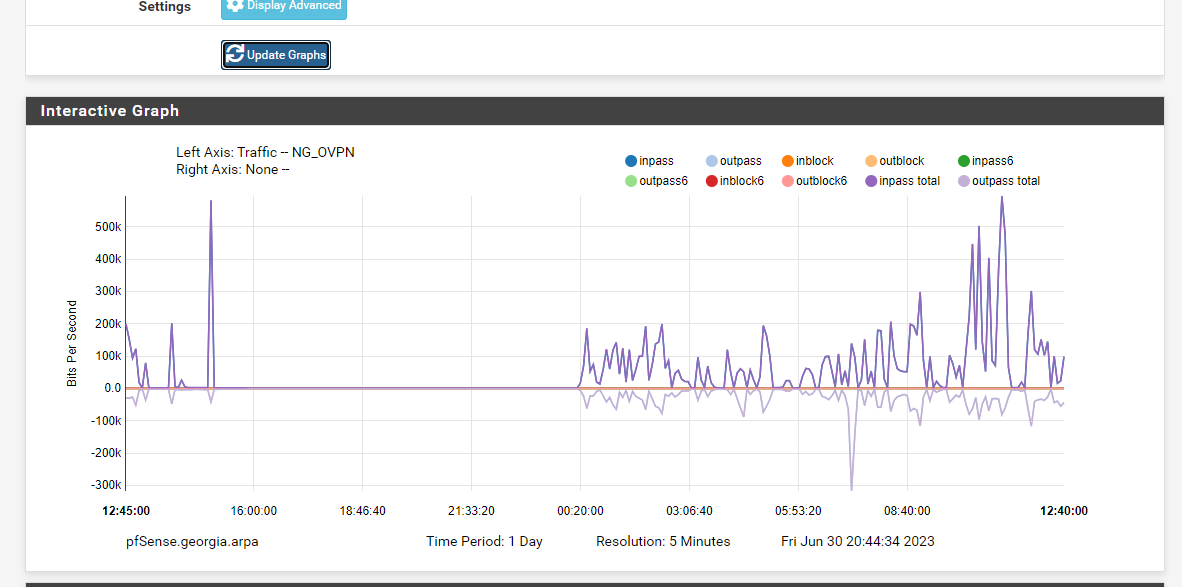
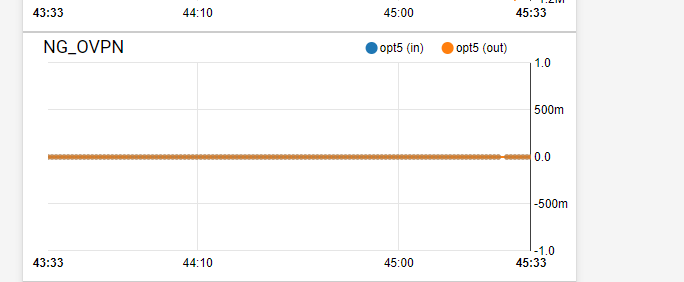
The Traffic Graph widget doesn't show the in\out traffic for the OpenVPN interfaces.
Files
 Updated by Danilo Zrenjanin over 2 years ago
Updated by Danilo Zrenjanin over 2 years ago
- Status changed from New to Confirmed
Tested on SG-3100 23.05.1 release. I can confirm this behavior.
 Updated by Kris Phillips over 2 years ago
Updated by Kris Phillips over 2 years ago
- File Screenshot from 2023-07-01 18-44-31.png Screenshot from 2023-07-01 18-44-31.png added
- File Screenshot from 2023-07-01 18-45-13.png Screenshot from 2023-07-01 18-45-13.png added
What is being done to reproduce this? I have two OpenVPN Client interfaces and the widget on the dashboard shows traffic just fine. Tested on amd64, so perhaps an architecture issue? See attached.
 Updated by Jim Pingle over 2 years ago
Updated by Jim Pingle over 2 years ago
It would help to know a few things, such as:
- Is DCO enabled or disabled?
- Is OpenVPN in tap or tun mode?
- Hardware platform
 Updated by Lev Prokofev over 2 years ago
Updated by Lev Prokofev over 2 years ago
In my case:
DCO enabled
Tun mode
Platform 5100
 Updated by Danilo Zrenjanin over 2 years ago
Updated by Danilo Zrenjanin over 2 years ago
I ran another test and this time, I disabled DCO. The traffic Graph widget was showing traffic.
The problem only occurs when DCO is enabled.
 Updated by Kris Phillips over 2 years ago
Updated by Kris Phillips over 2 years ago
I tested this with AES-128-GCM and DCO enabled and the Status --> Traffic Graphs still show traffic normally for me. Still not able to confirm this. I ran an iPerf test across an OpenVPN link and was able to see the link saturated on the traffic graph as normal.
 Updated by Jim Pingle over 2 years ago
Updated by Jim Pingle over 2 years ago
There is likely some other configuration factor contributing here then, such as tun/tap, subnet size, topology, etc. Though some of those are limited when DCO is in use, it's still worth expanding on which exact options are selected when it does/doesn't work.
 Updated by Danilo Zrenjanin over 2 years ago
Updated by Danilo Zrenjanin over 2 years ago
I tested again on a VM hosted on ProxMox with the factory default config file and the OpenVPN configured through the wizard using mostly default values.
Here is the Server Config when the Traffic Graphs widget shows a flat line.
dev ovpns1 verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 192.168.33.10 tls-server server 10.0.8.0 255.255.255.0 client-config-dir /var/etc/openvpn/server1/csc username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server1 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'OpenVPN_Cert' 1" lport 1194 management /var/etc/openvpn/server1/sock unix push "dhcp-option DNS 8.8.8.8" push "redirect-gateway def1" capath /var/etc/openvpn/server1/ca cert /var/etc/openvpn/server1/cert key /var/etc/openvpn/server1/key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server1/tls-auth 0 data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 data-ciphers-fallback AES-256-GCM allow-compression no persist-remote-ip float topology subnet explicit-exit-notify 1
Here is the server config when the Trafic Graph shows the corresponding values to the speed test measures.
dev ovpns1 disable-dco verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 192.168.33.10 tls-server server 10.0.8.0 255.255.255.0 client-config-dir /var/etc/openvpn/server1/csc username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server1 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'OpenVPN_Cert' 1" lport 1194 management /var/etc/openvpn/server1/sock unix push "dhcp-option DNS 8.8.8.8" push "redirect-gateway def1" capath /var/etc/openvpn/server1/ca cert /var/etc/openvpn/server1/cert key /var/etc/openvpn/server1/key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server1/tls-auth 0 data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 data-ciphers-fallback AES-256-GCM allow-compression no persist-remote-ip float topology subnet explicit-exit-notify 1 inactive 300
 Updated by Danilo Zrenjanin over 2 years ago
Updated by Danilo Zrenjanin over 2 years ago
The sole distinction lies in whether the DCO option was activated or deactivated on the server.
23.05.1-RELEASE (amd64) built on Wed Jun 28 03:57:27 UTC 2023 FreeBSD 14.0-CURRENT
 Updated by Lev Prokofev over 2 years ago
Updated by Lev Prokofev over 2 years ago
Can confirm if DCO is not active, the widget shows the correct graphs
 Updated by Kris Phillips over 2 years ago
Updated by Kris Phillips over 2 years ago
So I retested this today and now I'm seeing the same results with DCO enabled. The odd thing is that there is still little "blips" of activity, but then the rest of the graph is flat. See attached.
 Updated by Lev Prokofev over 2 years ago
Updated by Lev Prokofev over 2 years ago
The same behavior on
23.09-DEVELOPMENT (amd64) built on Fri Aug 18 06:05:19 UTC 2023 FreeBSD 14.0-ALPHA1
 Updated by Cody Gee over 1 year ago
Updated by Cody Gee over 1 year ago
This bug also affects SNMP. DCO enabled, Cacti graphs stopped populating. DCO disabled, traffic graphs.
24.03-RELEASE
 Updated by Danilo Zrenjanin over 1 year ago
Updated by Danilo Zrenjanin over 1 year ago
The issue persists in the 24.03
The traffic graph widget doesn't show traffic counts for the OpenVPN interface when DCO is enabled on the OpenVPN server.