Feature #14667
closedImprove SCTP support in ``filterlog``
100%
Description
FreeBSD 14.x includes more support for SCTP in the OS and in PF. There is a separate issue underway for allowing ports to be used with SCTP in firewall/NAT rules (#14640), but currently filterlog does not understand SCTP enough to know it has port data.
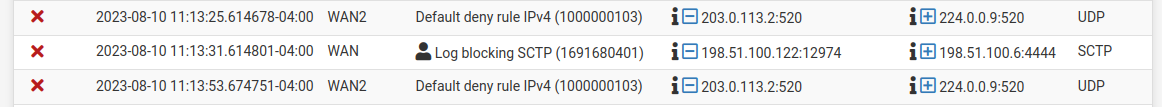
Preliminary support for SCTP log entries was added in #13940 but it is limited to source/destination IP address, not port data.
A log entry in filter.log for SCTP currently looks like:
Aug 8 11:20:04 vastra filterlog[18966]: 113,,,1686581398,lagg0.4090,match,block,in,4,0x0,,64,7895,0,none,132,sctp,132,198.51.100.122,198.51.100.15,datalength=112
Dumping the raw log device shows it is receiving and parsing the port data:
: tcpdump -vvvvi pflog0
tcpdump: listening on pflog0, link-type PFLOG (OpenBSD pflog file), snapshot length 262144 bytes
15:25:59.848897 IP (tos 0x0, ttl 64, id 27448, offset 0, flags [none], proto SCTP (132), length 132)
198.51.100.122.44259 > 198.51.100.15.4444: sctp
1) [INIT] [init tag: 2228743005] [rwnd: 1864135] [OS: 10] [MIS: 2048] [init TSN: 2039950541]
This implies the limitation is in the filterlog daemon.
Once filterlog understands SCTP port data and adds it in filter.log, then parse_firewall_log_line() in syslog.inc will need changed such that it knows SCTP has port data to parse, similar to TCP and UDP. For example, by adding a line for case '132': around line source:src/etc/inc/syslog.inc#L1099
Files
Related issues