Regression #14987
closed``Interface Address`` is no longer an option for outbound NAT targets
Added by Danilo Zrenjanin over 2 years ago. Updated about 2 years ago.
0%
Description
After upgrading to version 23.09, the option to choose a Tailscale address when defining an outbound NAT rule on the Tailscale interface is no longer available.
Steps to reproduce.
1.) Define Tailscale setup and confirm that it is active under Status/Tailscale
2.) Navigate to Firewall/NAT/Outbound and define a new mapping using the Tailscale interface.
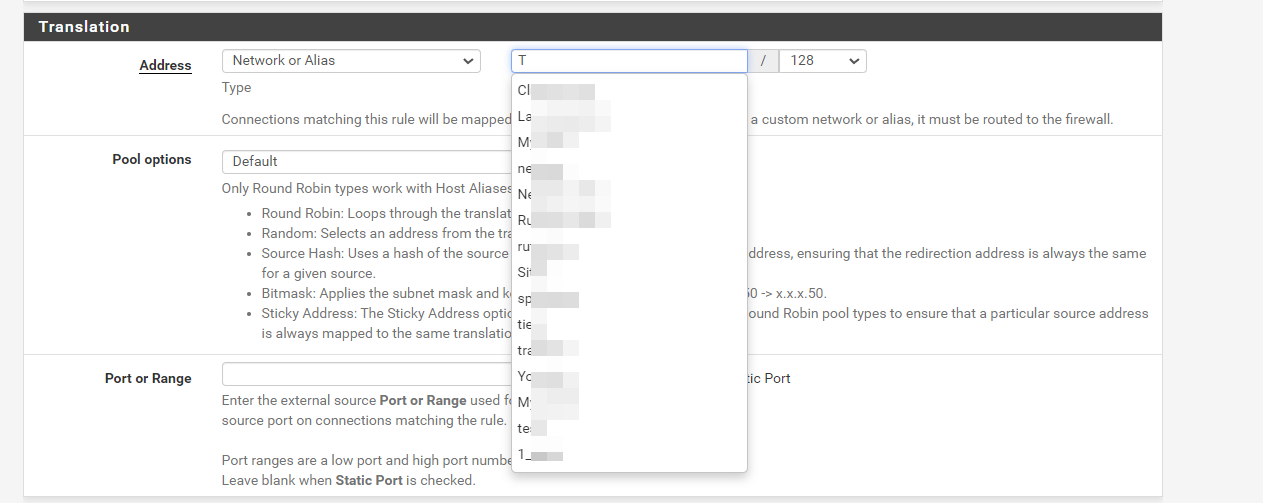
3.) Click on the Translation - Address drop-down menu.
4.) Notice that there is no option for a Tailscale address to choose.
Files
 Updated by Lev Prokofev over 2 years ago
Updated by Lev Prokofev over 2 years ago
- File clipboard-202311151300-hsm4m.png clipboard-202311151300-hsm4m.png added
- Status changed from New to Confirmed
Can confirm this,
tested on
23.09-RELEASE (amd64)
built on Tue Oct 31 22:56:00 MSK 2023
FreeBSD 14.0-CURREN
 Updated by aleksei prokofiev over 2 years ago
Updated by aleksei prokofiev over 2 years ago
- File clipboard-202311151456-gyk8a.png clipboard-202311151456-gyk8a.png added
- File clipboard-202311151456-da78t.png clipboard-202311151456-da78t.png added
- File clipboard-202311151458-eunfa.png clipboard-202311151458-eunfa.png added
- File clipboard-202311151458-tggqd.png clipboard-202311151458-tggqd.png added
Tested
23.09-RELEASE (amd64)
built on Tue Oct 31 22:56:00 MSK 2023
FreeBSD 14.0-CURRENT
If I assign Tailscale interface, in this case it is presented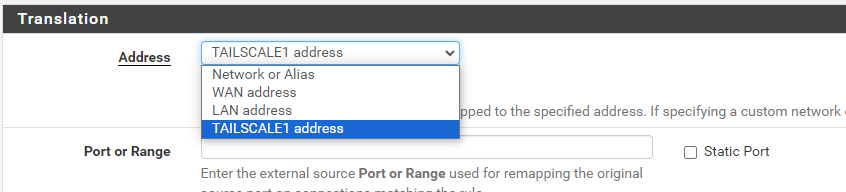
 Updated by Danilo Zrenjanin about 2 years ago
Updated by Danilo Zrenjanin about 2 years ago
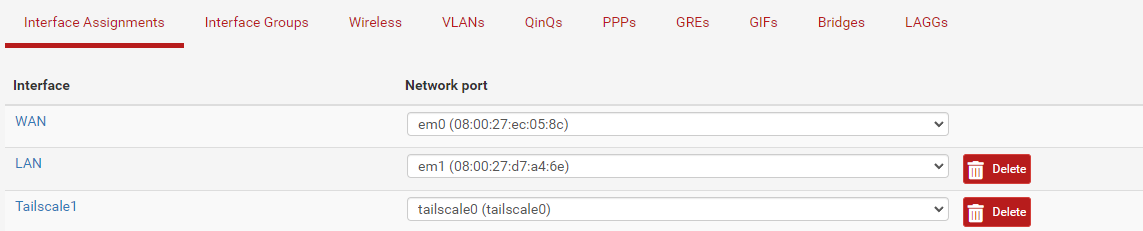
I've just tested and confirmed on 23.05.1 that there was no need to assign the Tailscale interface to have it in the list of available interfaces in the Outbound NAT rules.
Assigning a Tailscale interface in pfSense is wrong.
 Updated by Chad Wagner about 2 years ago
Updated by Chad Wagner about 2 years ago
Is there a workaround until this gets fixed?
 Updated by Mike Moore about 2 years ago
Updated by Mike Moore about 2 years ago
I second this issue. Is there a workaround.
If you are using tailscale to set a Site2Site VPN then traffic leaving the tailscale interface to a remote network learned within the tailnet must be sourced using the Tailscale interface.
Danilo - Are you saying that outbound SNAT rules are done automatically now?
 Updated by Mike Moore about 2 years ago
Updated by Mike Moore about 2 years ago
UPDATE:
I see the Tailscale interface has now been added back in 23.09.1
Please update the ticket to let us know if this is resolved permanently
 Updated by Chad Wagner about 2 years ago
Updated by Chad Wagner about 2 years ago
I am running 23.09.1. The Tailscale address is still missing from the pull-down menu in the translation section. In the setup video by Christian McDonald it says to not assign tailscale0 to an interface. Previously it appeared the "Tailscale address" selection was available in the outbound NAT rule creation without assigning the interface.
I have mine setup per the Tailscale website instructions, but it is basically making all UDP traffic have static NAT. I would rather have only Tailscale traffic be handled with static NAT.
 Updated by Danilo Zrenjanin about 2 years ago
Updated by Danilo Zrenjanin about 2 years ago
- File clipboard-202312150919-hksmq.png clipboard-202312150919-hksmq.png added
- File clipboard-202312150922-4btvs.png clipboard-202312150922-4btvs.png added
- File clipboard-202312150928-9zksy.png clipboard-202312150928-9zksy.png added
I've tested on 23.09.1. Indeed, there is no Tailscale address from the drop-down menu in the translation section.
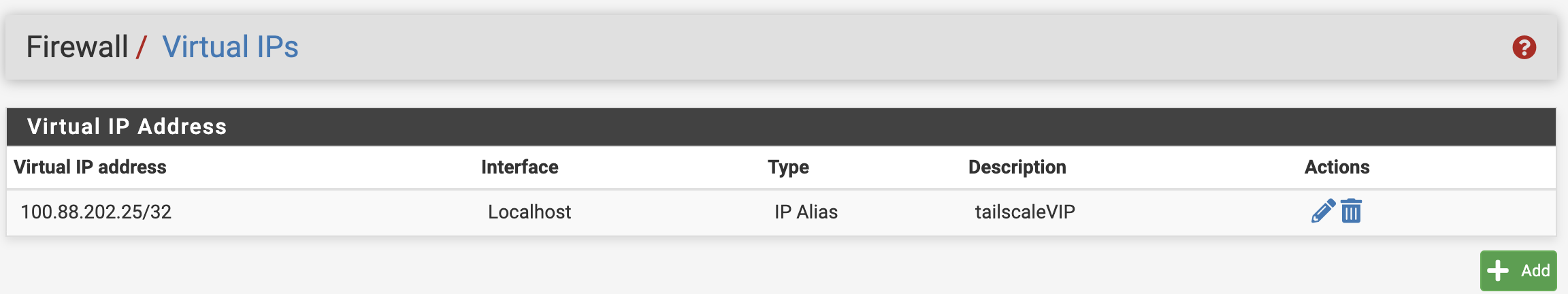
As a workaround, you can define an IP Alis VIP using localhost as the Parent interface and the Tailscale address of that node for IP.
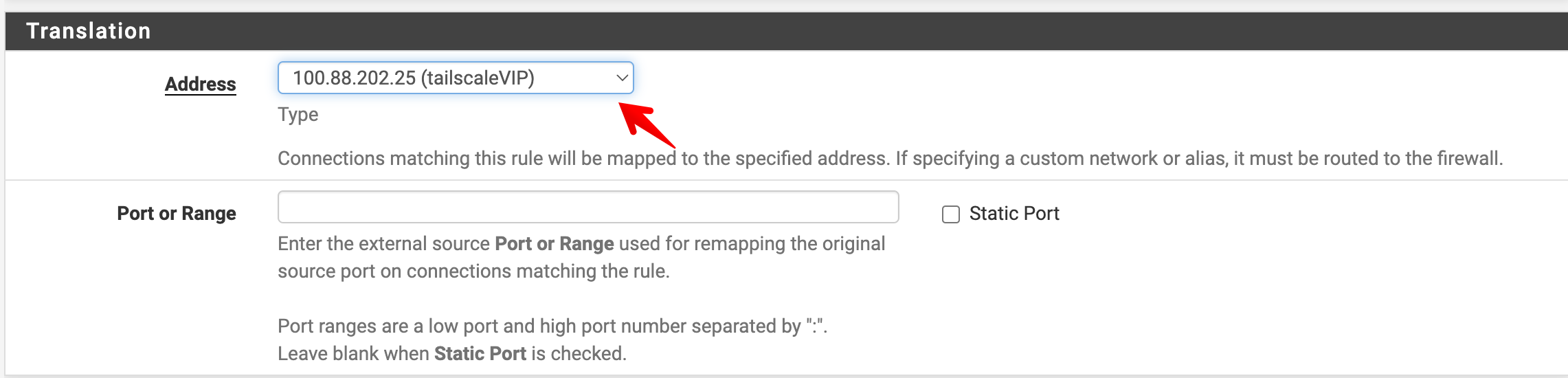
In the outbound NAT rule, the VIP address defined in the previous step will be available in the drop-down menu.
Once the outbound NAT rule is configured on both sides, the traffic flows as intended in both directions.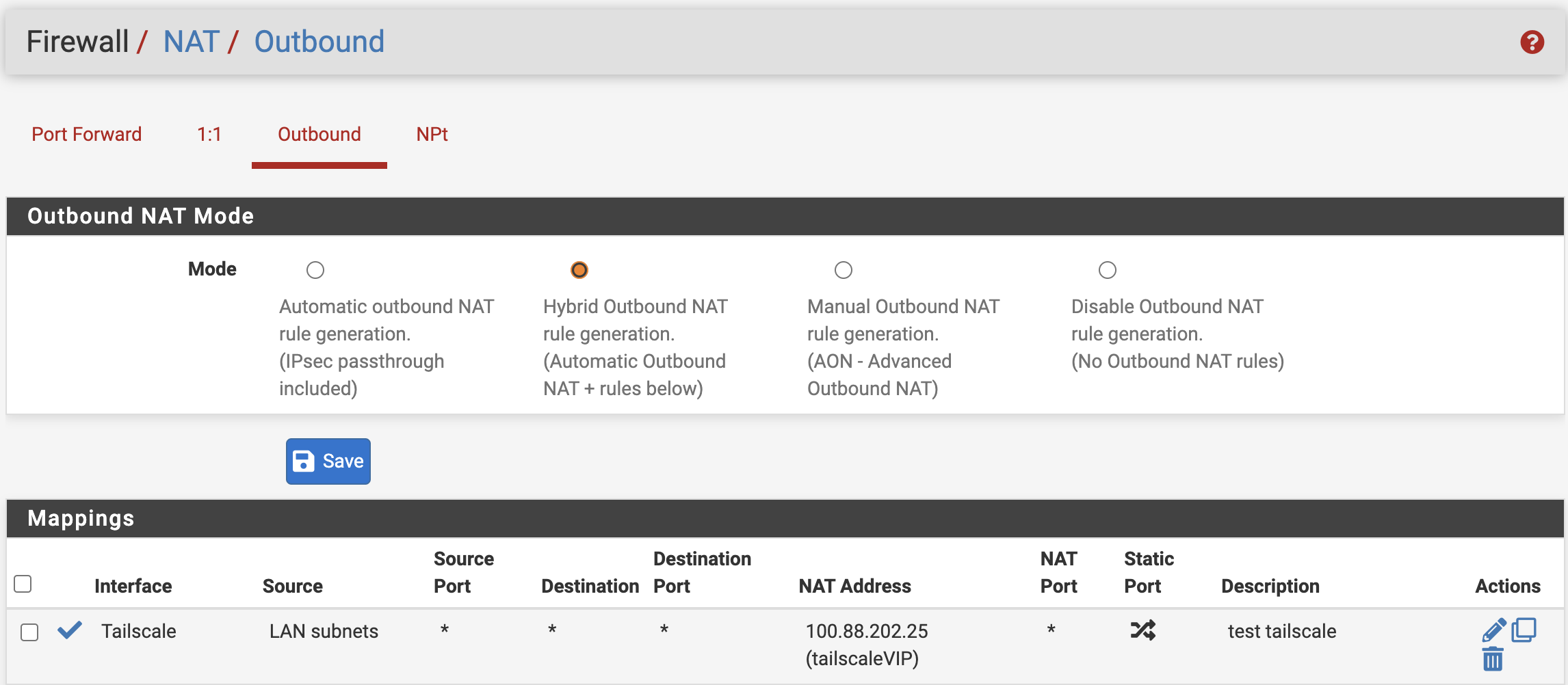
 Updated by Marcos M about 2 years ago
Updated by Marcos M about 2 years ago
- Project changed from pfSense Packages to pfSense
- Subject changed from Tailscale Address option is missing in Translation Address section under Firewall/NAT/Outbound to ``Interface Address`` is no longer an option for outbound NAT targets
- Category changed from Tailscale to Rules / NAT
- Status changed from Confirmed to Not a Bug
- Assignee deleted (
Christian McDonald) - Affected Version set to 2.7.2
- Release Notes set to Default
- Affected Architecture All added
- Expose
<interface> subnetsaliases in source/destination - Expose
<interface group> networksaliases in source/destination - Alias popup preview on the
NAT Addressfield - Better error handling on rules to avoid filter reload failures
With other VPN types such as OpenVPN, IPsec, or WireGuard, the option isn't needed or simply doesn't apply. However, Tailscale is an edge case that indeed benefits from having the "Interface Address" option given that it cannot have an interface assignment. In this case, the address should be entered by selecting Network or Alias. If there's a use-case that necessitates frequently changing the interface address, an option for this edge case could be considered.
 Updated by Jonathan Lee about 2 years ago
Updated by Jonathan Lee about 2 years ago
Does this cause issues with layer 2 experimental rules? They are MAC address or interface based.