Todo #15266
closedPrevent usage of the default password in User Manager accounts
Added by Jim Pingle about 2 years ago. Updated almost 2 years ago.
100%
Description
Currently we detect in the GUI when the admin account is using the default password ("pfsense") and print a warning message: source:src/usr/local/www/head.inc#L564
We should change that to check any account (not just admin) and force a password change during one or more of the user's initial interactions, for example:
- During the setup wizard
- GUI login any time the password matches the default password
- Shell (console or SSH) login any time the password matches the default password
- Possibly during the installation process
We should also not allow the user to change their password to any variation of "pfsense" in upper/lower/mixed case.
Files
| clipboard-202403141351-mfloc.png (153 KB) clipboard-202403141351-mfloc.png | Danilo Zrenjanin, 03/14/2024 12:51 PM | ||
| clipboard-202403161624-tfmug.png (168 KB) clipboard-202403161624-tfmug.png | Jordan G, 03/16/2024 09:24 PM | ||
| clipboard-202403302008-x67k0.png (23.1 KB) clipboard-202403302008-x67k0.png | Jordan G, 03/31/2024 01:08 AM |
 Updated by Bill Meeks about 2 years ago
Updated by Bill Meeks about 2 years ago
I would ask why make this change? I think the current warning is sufficient.
I would be okay with forcing a password change on the initial login, but I really would resent not being able to then choose a password of my choice including putting "pfsense" right back in there if I wanted to. And once that initial prompt and forced password change is shown, it should not be shown again even if the user purposefully put "pfsense" right back in there. I create a lot of test VMs in my lab environment and leave them with the default login for simplicity.
I personally really hate this type of mother henning in software. Let me as a user decide how I want to handle passwords in my systems.
 Updated by Jim Pingle about 2 years ago
Updated by Jim Pingle about 2 years ago
Not only are there more and more stories about equipment being compromised due to default passwords and being wide open to the internet (not pfSense primarily, and definitely user error, but partially avoidable either way), there are also legal/regulatory reasons outside of our control.
We could allow someone to change it back to "pfsense" but that could still leave someone vulnerable.
These days with password managers and SSH keys the actual passwords rarely matter much since it's not typed by hand all that often in many cases.
 Updated by Bill Meeks about 2 years ago
Updated by Bill Meeks about 2 years ago
Jim Pingle wrote in #note-2:
Not only are there more and more stories about equipment being compromised due to default passwords and being wide open to the internet (not pfSense primarily, and definitely user error, but partially avoidable either way), there are also legal/regulatory reasons outside of our control.
We could allow someone to change it back to "pfsense" but that could still leave someone vulnerable.
These days with password managers and SSH keys the actual passwords rarely matter much since it's not typed by hand all that often in many cases.
The legal/regulatory angle I understand having worked in the very tightly regulated nuclear power industry for my entire career.
I will get over it <grin>, but it is just a pet peeve of mine when software won't let me do something I consciously want to do for a particular situation or reason. Of course, I would never deploy something to production with a default password still set, much less then leave it open to the Internet. But I get that some folks might do that.
I will go back in my house now, get back in my chair, and continue watching reruns of The Andy Griffith Show. You kids can play on my lawn -- just don't make a mess. LOL!
 Updated by Jim Pingle about 2 years ago
Updated by Jim Pingle about 2 years ago
- Project changed from pfSense to pfSense Plus
- Category changed from Authentication to Authentication
- Target version changed from 2.8.0 to 24.03
- Plus Target Version deleted (
24.03)
Moving this so it only gets applied to Plus, since Plus is the only version for appliances where those restrictions have to apply. CE can stay as-is.
 Updated by Jim Pingle about 2 years ago
Updated by Jim Pingle about 2 years ago
- Status changed from New to In Progress
- % Done changed from 0 to 30
Partial progress: Setup wizard changes are done.
https://gitlab.netgate.com/pfSense/factory/-/commit/e79b4b227898396bfa7396d2eae70ca447adfd35
 Updated by Danilo Zrenjanin almost 2 years ago
Updated by Danilo Zrenjanin almost 2 years ago
That part looks good. The setup wizard doesn't allow the default password to be defined.
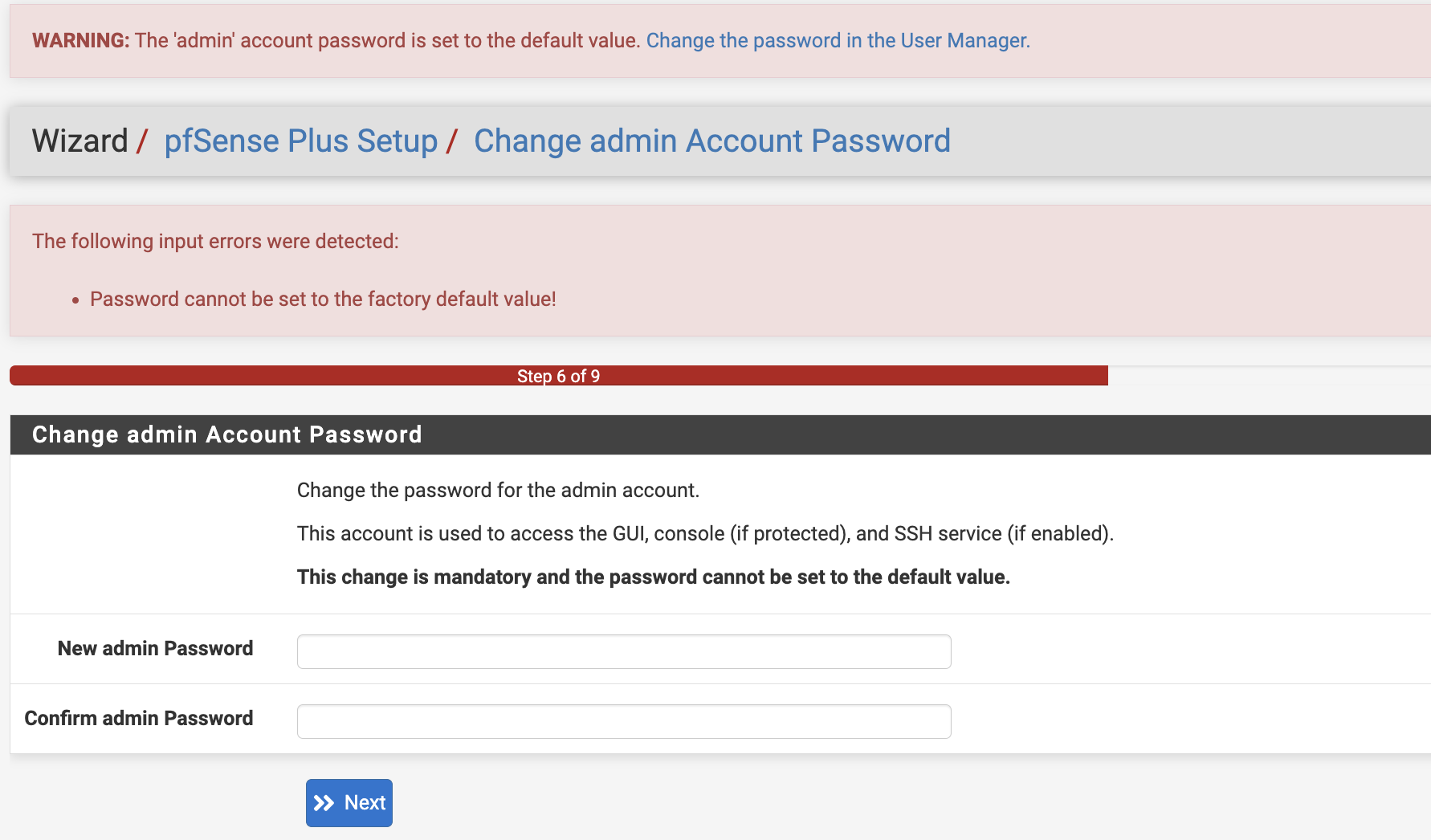
 Updated by Jim Pingle almost 2 years ago
Updated by Jim Pingle almost 2 years ago
- Status changed from In Progress to Feedback
- % Done changed from 30 to 100
This is now in and complete.
tl;dr: Passwords are now a little more strict on both Plus and CE. Plus forces password changes if the password is set to default or the username.
Summary of changes:
- Plus/CE: Backend support added for password validation rules which control allowed values for passwords set on user accounts.
- Plus/CE: Most methods of changing the password now also display hints to the user about password requirements.
- Plus/CE: Passwords can no longer be set to the same value as the username
- Plus: Passwords can also not be set to the default value "pfsense"
- Plus/CE: Setup wizard validates the password before proceeding
- Plus: Setup wizard requires the user to change the password and will not proceed until the password is changed to a valid value.
- Plus/CE: Warning banners about insecure passwords have been improved.
- Plus/CE: Banner now links to the self-service password manager if the current user password is insecure and the user has access to that page, otherwise it links to the user manager entry for the account.
- Plus/CE: Separate banner is displayed when logging with an account other than "admin" if the "admin" account password is insecure and the user has sufficient privileges to change it. This warning links to the user manager entry for the "admin" account.
- Plus/CE: Warning banners are not displayed if the user does not have access to change the password.
- Plus/CE: Self-service password page is now more informative and user-friendly. It's now available in the menu and as a tab in the user manager.
- Plus: Page also displays an additional warning banner if the password is invalid to make it more clear why the user was directed there.
- Plus: GUI forces password change if the password is "insecure" (equal to the username or the default value)
- If it is the first time visiting the GUI, the user can change the password using the wizard
- For existing installs, the user is directed to the password reset screen.
- Plus/CE: Shell scripts added to interact with the user manager
usermgrwhoami- Prints information about the current logged-in user from the User Managerusermgrpasswd- Checks or changes passwords in the User Manager
- Plus/CE: Reset admin account from shell menu now prompts for new password, it does not reset to factory default password.
- Plus: Shell menu forces password change if the admin account password is insecure.
- If the user changed the password in the GUI they can bypass this with `ctrl-c` -- It will re-check the password and either continue to the menu if it's OK or logout if the password has not been changed.
Reminder: Access to the self-service password page is governed by the "WebCfg - System: User Password Manager" privilege, so non-admin users should have that privilege added to their account/group if they should be able to change their own user manager password.
 Updated by Jim Pingle almost 2 years ago
Updated by Jim Pingle almost 2 years ago
- Subject changed from Force user to change password to Prevent usage of the default password in User Manager accounts
 Updated by Jordan G almost 2 years ago
Updated by Jordan G almost 2 years ago
Upon updating to build 24.03.b.20240314.0323 and logging in, you are immediately taken to password reset (if it was still default). System allowed me to use a 3 character password, which I verified by logging out and back in again. Confirmed you cannot re-use the original default "pfsense" when trying to change the password again. Using the console password reset only reset to default, it did not allow entering a new password and shell menu was accessible prior to changing password in the web GUI and is also once again following it being set back to the default using the console menu reset option and rebooting.

 Updated by Jim Pingle almost 2 years ago
Updated by Jim Pingle almost 2 years ago
That build doesn't have all of the final changes, it has to be a build from the 15th or later, which hasn't been successful yet.
 Updated by Danilo Zrenjanin almost 2 years ago
Updated by Danilo Zrenjanin almost 2 years ago
Jim Pingle wrote in #note-10:
This is now in and complete.
tl;dr: Passwords are now a little more strict on both Plus and CE. Plus forces password changes if the password is set to default or the username.
Summary of changes:
- Plus/CE: Backend support added for password validation rules which control allowed values for passwords set on user accounts.
- Plus/CE: Most methods of changing the password now also display hints to the user about password requirements.
- Plus/CE: Passwords can no longer be set to the same value as the username
- Plus: Passwords can also not be set to the default value "pfsense"
All the above works as expected ^^^.
- Plus/CE: Setup wizard validates the password before proceeding
- Plus: Setup wizard requires the user to change the password and will not proceed until the password is changed to a valid value.
This is true. But, at the second step, the wizard prompts you to change the password. However, upon completing this step, the wizard doesn't proceed and instead remains on the System/User Password Manager page.
Tested against:
24.03-BETA (amd64) built on Fri Mar 22 17:08:00 UTC 2024 FreeBSD 15.0-CURRENT
 Updated by Jim Pingle almost 2 years ago
Updated by Jim Pingle almost 2 years ago
Danilo Zrenjanin wrote in #note-14:
- Plus: Setup wizard requires the user to change the password and will not proceed until the password is changed to a valid value.
This is true. But, at the second step, the wizard prompts you to change the password. However, upon completing this step, the wizard doesn't proceed and instead remains on the System/User Password Manager page.
I can't reproduce that here. I can set a new password and proceed past that screen. Is it displaying an error message of some sort when it won't proceed?
 Updated by Jim Pingle almost 2 years ago
Updated by Jim Pingle almost 2 years ago
I think I was able to reproduce that issue finally. Starting from a fresh install or factory reset the user was being sent to the password reset page when it should have been continuing through the wizard instead. I committed a fix.
 Updated by Danilo Zrenjanin almost 2 years ago
Updated by Danilo Zrenjanin almost 2 years ago
Another inconsistency is that when performing a clean install in the console, you will be prompted to change the default password before the console menu appears. Once you have changed the password, you will see the console menu. The next step is to access the GUI, which will automatically start the wizard. In the final step of the wizard, you will be prompted to change the password again, even if you already did so from the console.
The wizard should check and skip the last step (changing the password) if it's not set to the default value.
Tested against:
24.03-BETA (amd64) built on Fri Mar 29 6:00:00 UTC 2024 FreeBSD 15.0-CURRENT
 Updated by Jordan G almost 2 years ago
Updated by Jordan G almost 2 years ago
on 20240329-0600 build after restoring a backup with default password, both console and gui requested changing the password. The console displays instructions for cancelling in case you have already changed password in the web interface. 1, 2 and 3 character passwords are still accepted and work to login with admin account.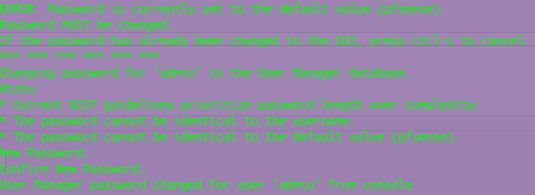
 Updated by Jim Pingle almost 2 years ago
Updated by Jim Pingle almost 2 years ago
Danilo Zrenjanin wrote in #note-17:
Another inconsistency is that when performing a clean install in the console, you will be prompted to change the default password before the console menu appears. Once you have changed the password, you will see the console menu. The next step is to access the GUI, which will automatically start the wizard. In the final step of the wizard, you will be prompted to change the password again, even if you already did so from the console.
The wizard should check and skip the last step (changing the password) if it's not set to the default value.
The wizard has always prompted for changing the password no matter what. Some people like having the option if they are using the wizard again later.
You can skip by it so long as the password is not set to a problematic value.
 Updated by Jim Pingle almost 2 years ago
Updated by Jim Pingle almost 2 years ago
- Status changed from Feedback to Resolved
Jordan G wrote in #note-18:
on 20240329-0600 build after restoring a backup with default password, both console and gui requested changing the password. The console displays instructions for cancelling in case you have already changed password in the web interface. 1, 2 and 3 character passwords are still accepted and work to login with admin account.
That's all as expected. The only password rules we have currently are to reject the default password and when the password matches the username. There are no other rules governing length or complexity at this time.