Feature #11556
closedKill states using the pre-NAT address
0%
Description
Assume you have an external IP XXX
And an OpenVPN net 192.168.200.0/0
After OpenVPN client connects it gets an IP 192.168.200.2
Now let's use States to see and kill all states for 192.168.200.2
There are lots of states look like this:
WAN tcp XXX:49313 (192.168.200.2:62472) -> <some_IP>:443 TIME_WAIT:TIME_WAIT 84 / 108 6 KiB / 129 KiB
And they don't get killed.
Expected - all states associated with 192.168.200.2 killed, or there is an option to select all and allow kill.
Files
Related issues
 Updated by Jim Pingle almost 5 years ago
Updated by Jim Pingle almost 5 years ago
- Subject changed from Kill all states associated with an host IP NET address to Kill all states associated with a NAT address
- Category changed from NAT Reflection to Rules / NAT
Correcting the category and subject
The ask here is for a way to kill based on the NAT address in the state instead of the source or destination.
 Updated by Marcos M almost 5 years ago
Updated by Marcos M almost 5 years ago
I can confirm this is currently an issue.
 Updated by Viktor Gurov about 4 years ago
Updated by Viktor Gurov about 4 years ago
- Related to Feature #12807: Clear Active Secondary WAN Connections added
 Updated by Marcos M about 3 years ago
Updated by Marcos M about 3 years ago
- Related to Bug #13226: Disconnecting a user from Captive Portal may allow previously established connections to continue added
 Updated by Kristof Provost over 2 years ago
Updated by Kristof Provost over 2 years ago
Proposed implementation in https://reviews.freebsd.org/D42312 (test in https://reviews.freebsd.org/D42313)
This will still need some PHP glue too.
 Updated by Marcos M about 2 years ago
Updated by Marcos M about 2 years ago
- Tracker changed from Bug to Feature
- Subject changed from Kill all states associated with a NAT address to Kill states using the pre-NAT address
- Status changed from New to Feedback
- Assignee changed from Reid Linnemann to Marcos M
- Target version set to 2.8.0
- Plus Target Version set to 24.03
 Updated by Marcos M about 2 years ago
Updated by Marcos M about 2 years ago
- Assignee changed from Marcos M to Kristof Provost
https://gitlab.netgate.com/pfSense/FreeBSD-ports/-/merge_requests/381
The php pfSense module has been updated to implement the new functionality.
Killing states is done in the following scenarios - the fix applies to all of them:- killing states for the previous IP when the WAN IP changes
- killing states for locked out clients (sshguard or captive portal)
- killing states to the gateway when resetting dpinger / gateway monitoring
- killing filtered and specific states in Diagnostics > States
Merged in 77282e83a0fb1f41a395ddd0ad1b6619301666be.
 Updated by Chris Linstruth about 2 years ago
Updated by Chris Linstruth about 2 years ago
Please also see scenario:
killing states when a pass rule with a schedule expires:
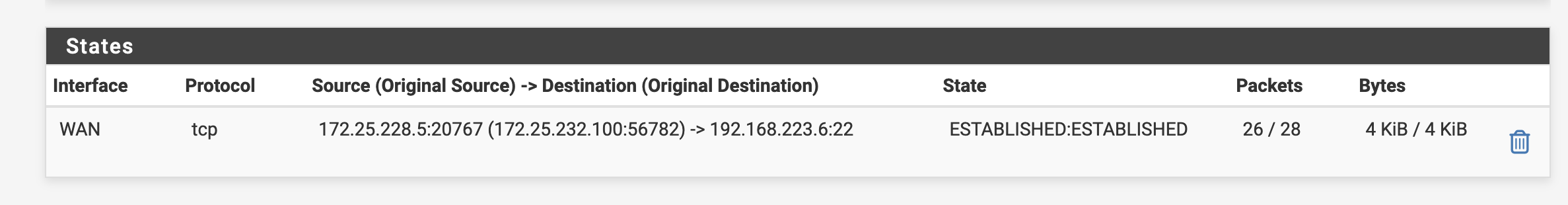
 Updated by Chris Linstruth about 2 years ago
Updated by Chris Linstruth about 2 years ago
- Status changed from Feedback to In Progress
 Updated by Kristof Provost about 2 years ago
Updated by Kristof Provost about 2 years ago
Hi Chris,
It's not clear to me what the problem is in comment 9. Is that state not getting killed when you'd expect it to be?
If so, what version are you testing? Can you describe the entire scenario (i.e. how the state was established, and why it was expected to be killed)?
 Updated by Chris Linstruth about 2 years ago
Updated by Chris Linstruth about 2 years ago
It is killing the LAN side but not the WAN side.
It was an ssh session on a rule with a schedule.
When the schedule expires, the LAN session is killed but not the WAN. This is an additional scenario to those listed here:
killing states for the previous IP when the WAN IP changes
killing states for locked out clients (sshguard or captive portal)
killing states to the gateway when resetting dpinger / gateway monitoring
killing filtered and specific states in Diagnostics > StatesI don't think there needs to be anything more done to the pf. I think it might just be that -k nat needs to be added to the php in that case. But that's just a guess on my part.
 Updated by Marcos M about 2 years ago
Updated by Marcos M about 2 years ago
- Assignee changed from Kristof Provost to Marcos M
 Updated by Marcos M about 2 years ago
Updated by Marcos M about 2 years ago
- Status changed from In Progress to Resolved
I separated that issue into its own report: https://redmine.pfsense.org/issues/15252